Entra Internet Access: Secure Access to Internet Resources and SaaS Apps

In this article, will walk you through the capabilities of Microsoft Entra Internet Access to block or allow secure access to Internet resources and Software as a Service (SaaS) apps through Global Secure Access client and Conditional Access.
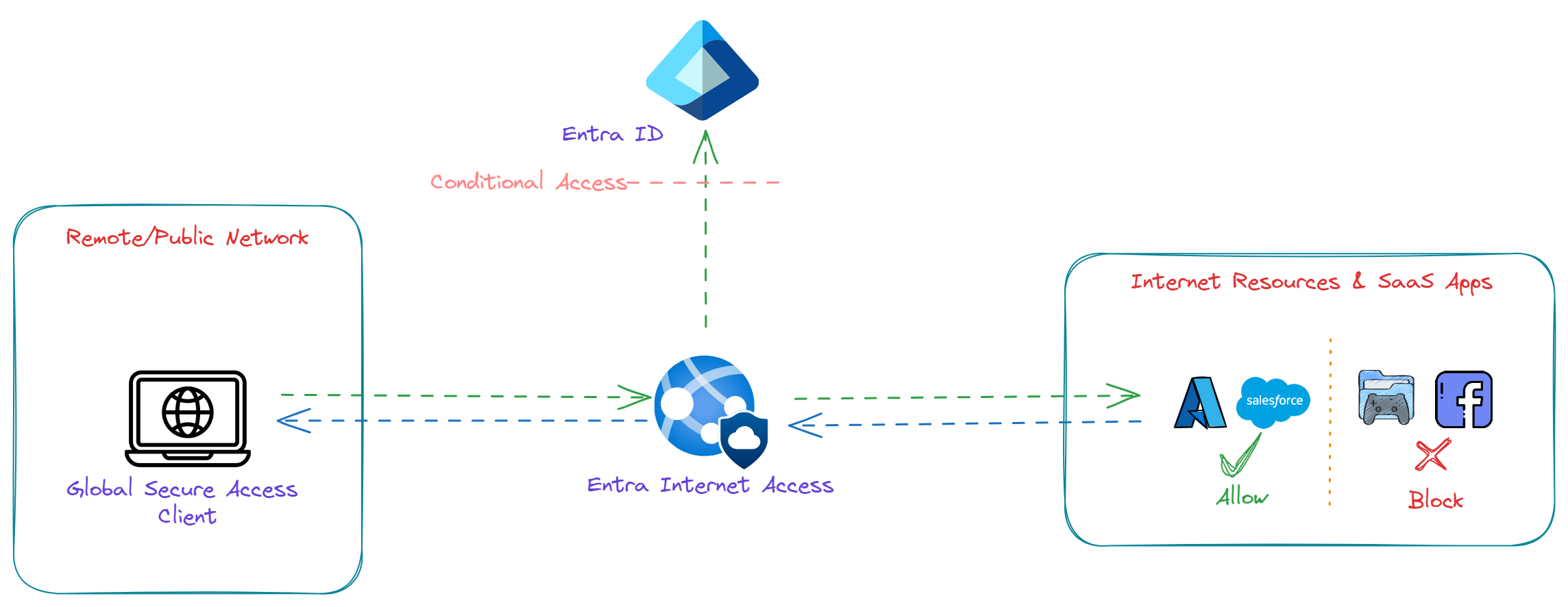
Microsoft Entra Internet Access provides an identity centric Secure Web Gateway (SWG) solution for SaaS applications and other internet resources by protecting users, devices and data from internet's wide threat landscape with a Conditional Access and visibility through traffic logs.
Entra Internet Access filters internet traffic using Web Content filtering based on domain names. Entra Internet Access integrates Web content filtering policies with Entra ID and Conditional Access which results in filtering policies that are user-aware and context-aware.
Currently Web Content filtering is limited to Web Category filtering and FQDN filtering.
Web Category Filtering: List of predefined web categories such as Games, Social Networking, etc.,
FQDN Filtering: Based on Fully Qualified Domain Names and wildcards such as zerotrust.how, *.zerotrust.how
Security profiles are objects used to group web content filtering policies and deliver them through Conditional Access policies. Each security profile can contain multiple filtering policies and each security profile can be associated with multiple Conditional Access policies.
Within a security profile, policies are enforced according to priority ordering with 100 being the highest priority and 65,000 being the lowest priority.
Prerequisites
Required Roles
- Global Secure Access Administrator role: Required to setup and manage Entra Private Access
- Conditional Access Administrator or Security Administrator role; Required to create and interact with Conditional Access policies
Supported Devices
- Windows 10/11 (Microsoft Entra Joined) (Hyper-V hosted aren't supported yet)
- Android
- MacOS (Early Access - Private Preview)
- iOS (Early Access - Private Preview)
Enable Entra Internet Access
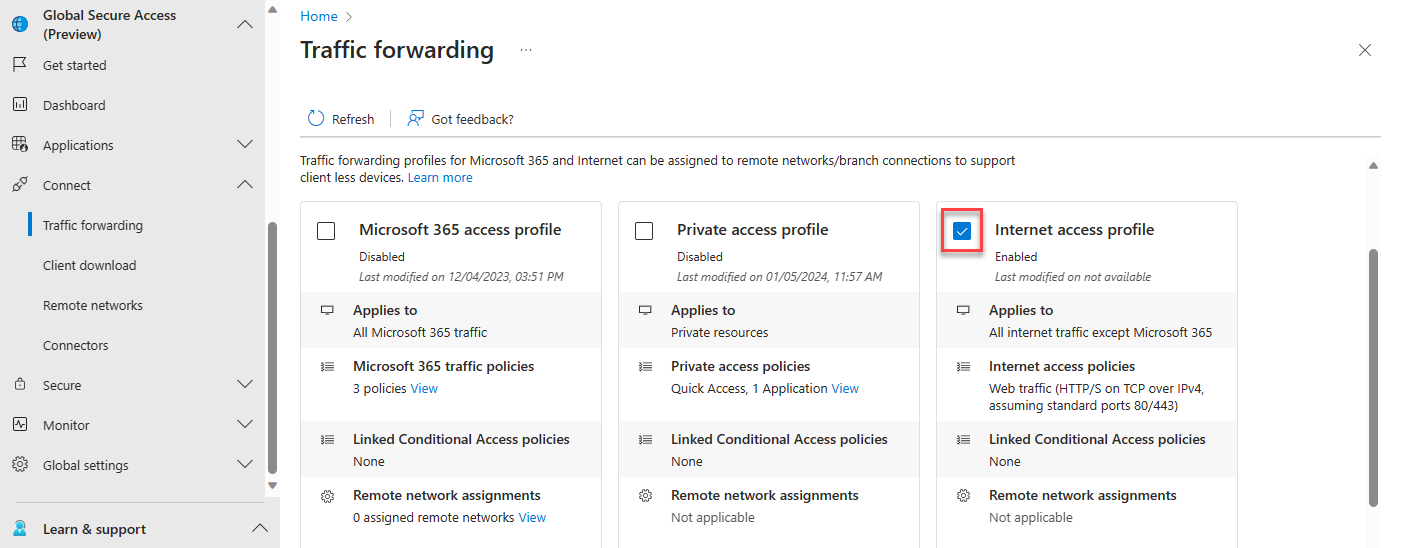
Login to entra.microsoft.com, Navigate to Global Secure Access -> Connect -> Traffic forwarding then enable Internet access profile.
Download and Install Global Secure Access Client
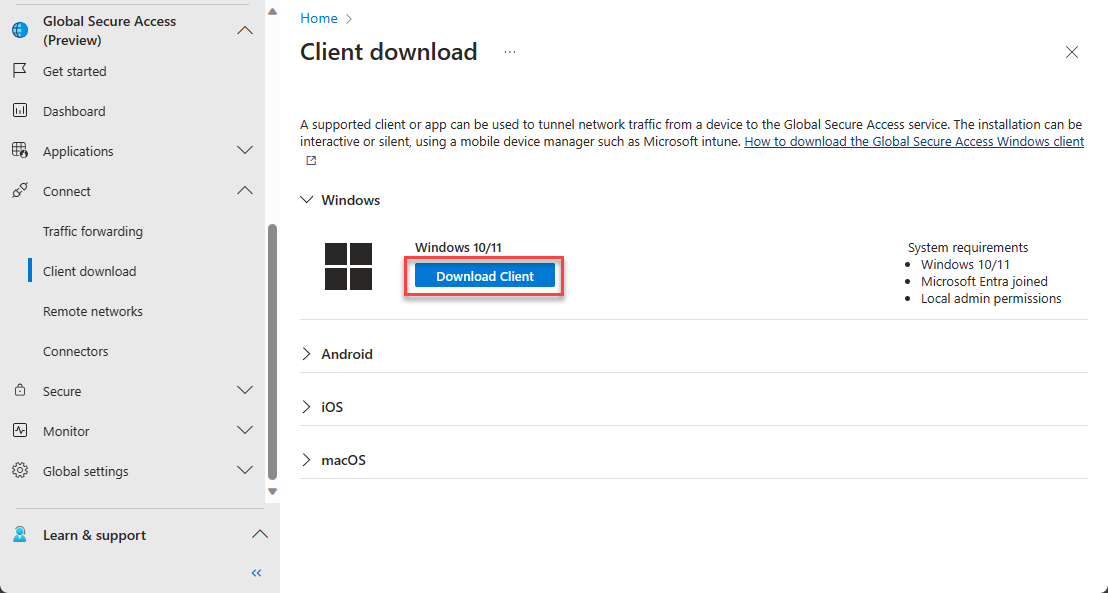
Download the client from Global Secure Access -> Connect -> Client download page.
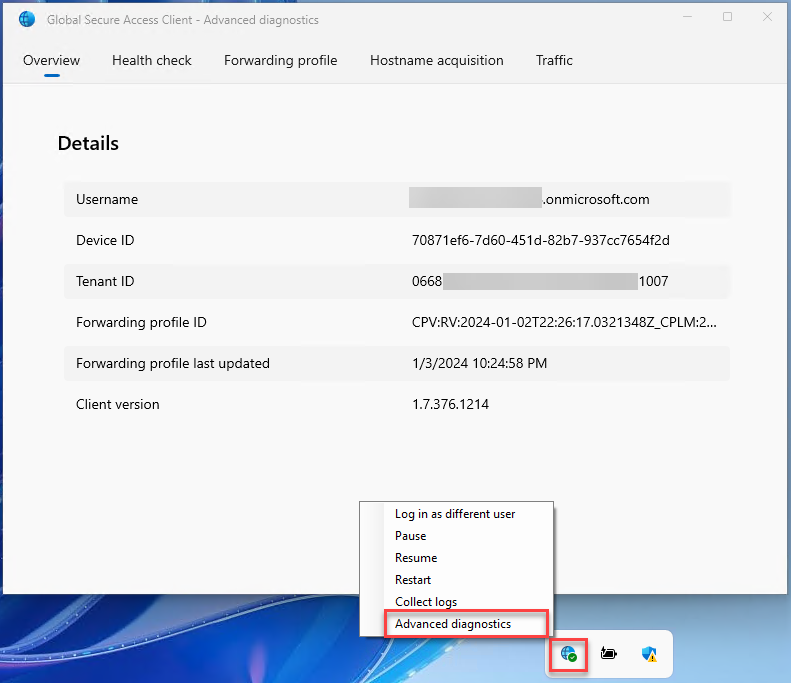
Install GSA client on a Entra joined Windows 10/11 device. Once installed, verify the service is running by opening the Advanced diagnostics and see the Overview and Health check.
Create Web Content Filtering Policy
Create two web content filtering policies; one is based on web category and another one is for FQDN.
Web Category Policy
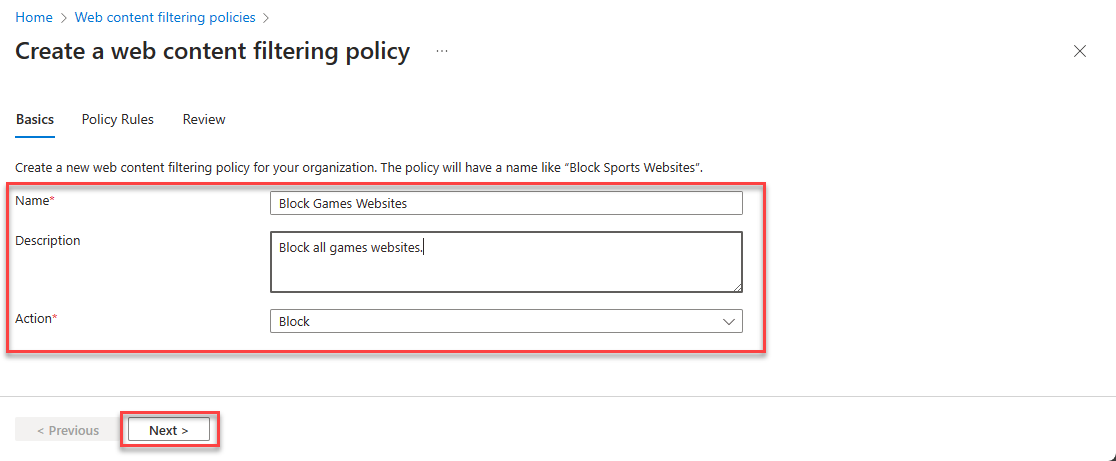
To create Web Category policy: Navigate to Global Secure Access -> Secure -> Web content filtering policies. Select Create policy.
- Enter Name (example: Block Some Websites)
- Select Action (Block or Allow). In this case, it is Block rule. Click on Next
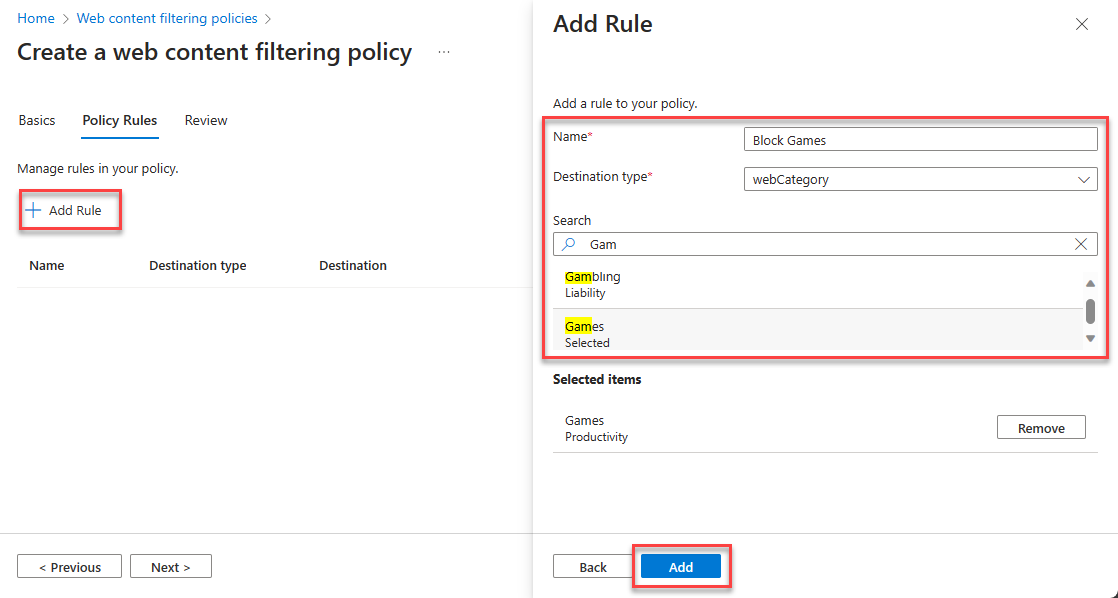
- Select Add Rule
- Enter Name (example: Block Games)
- Select Destination type as webCategory
- Search and select web category (example Games)
- Click on Add then Next
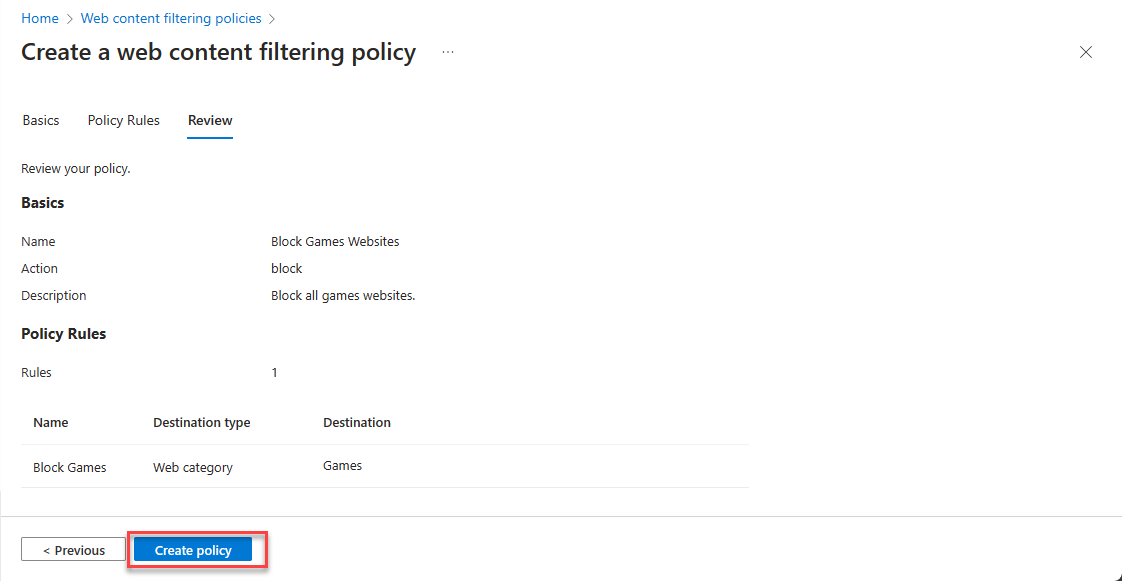
- Review the policy rules and click on Create policy
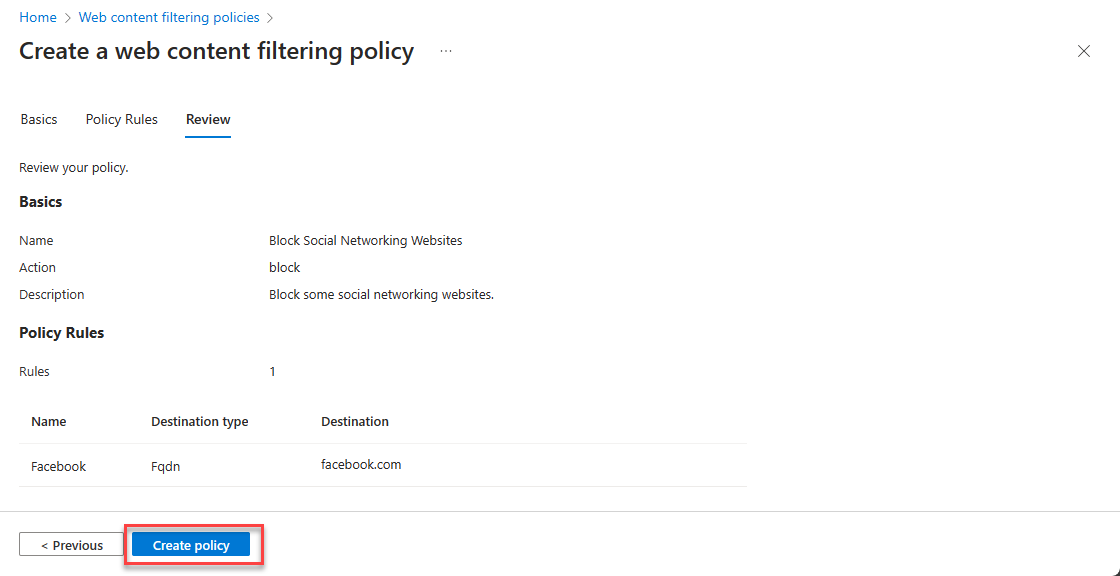
FQDN Policy
To create FQDN policy: Navigate to Global Secure Access -> Secure -> Web content filtering policies. Select Create policy.
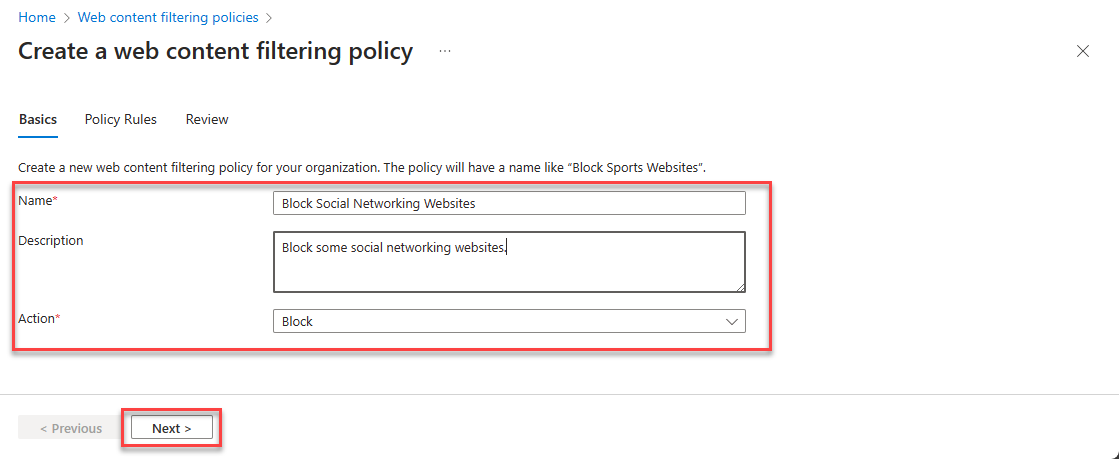
- Enter Name (example: Block Social Networking Websites)
- Select Action (Block or Allow). In this case, it is Block rule. Click on Next
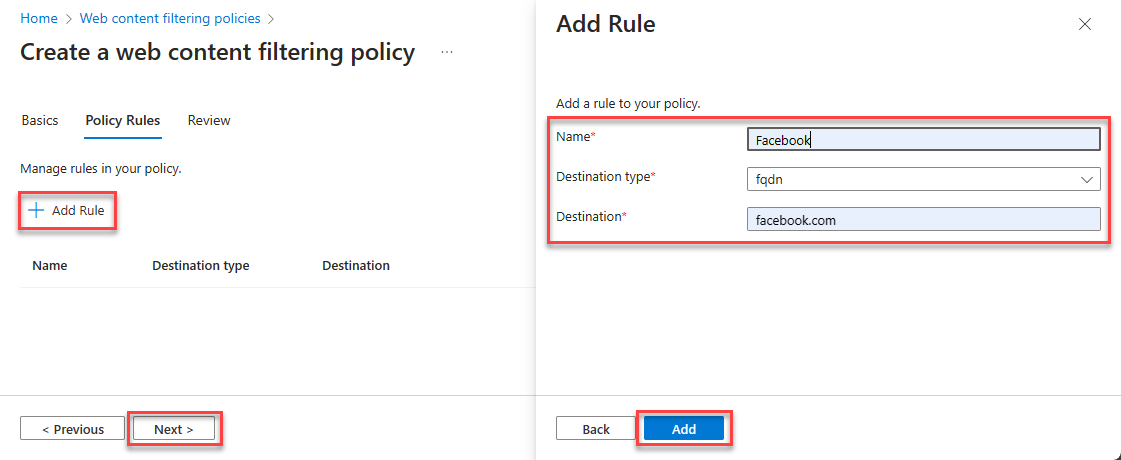
- Select Add Rule
- Enter Name (example: Facebook)
- Select Destination type as fqdn
- Enter Destination (example: facebook.com)
- Click on Add then Next
- Review the policy rules and click on Create policy
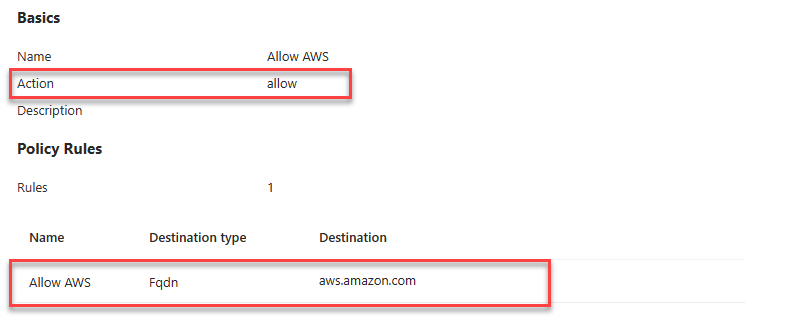
Likewise, create allow policies for SaaS resources to secure the traffic through Global Secure Access.
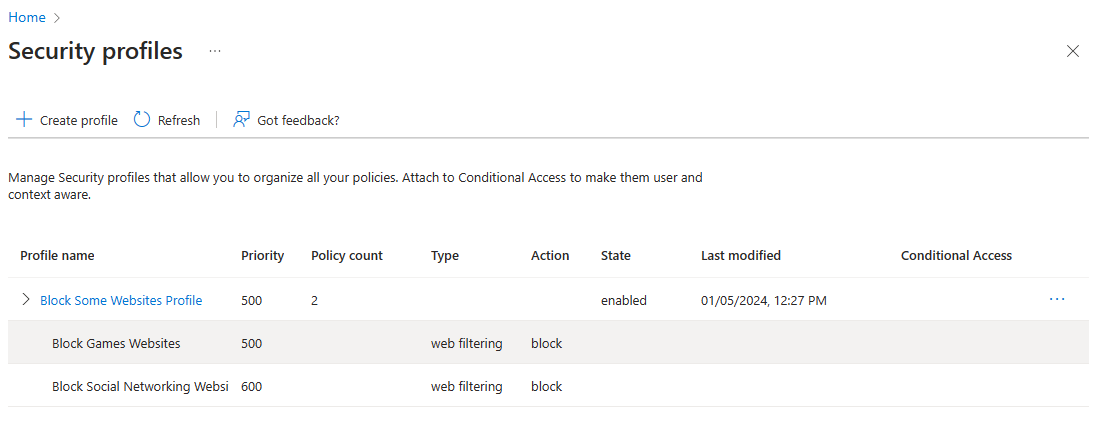
Create Security Profiles
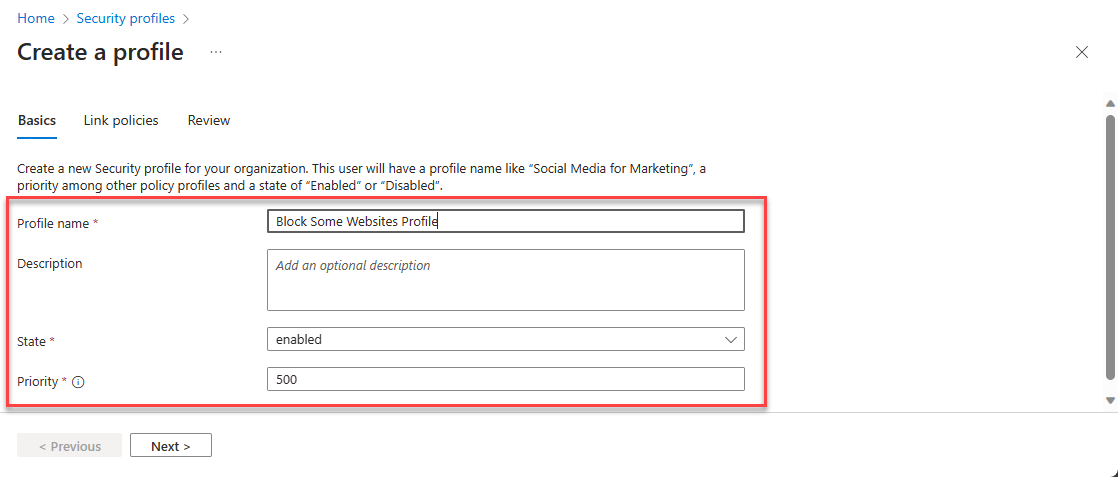
To create Web Category policy: Navigate to Global Secure Access -> Secure -> Security profiles. Select Create profile.
- Enter Profile name (example: Block Websites Profile)
- Select State as Enabled
- Enter Priority and Click on Next
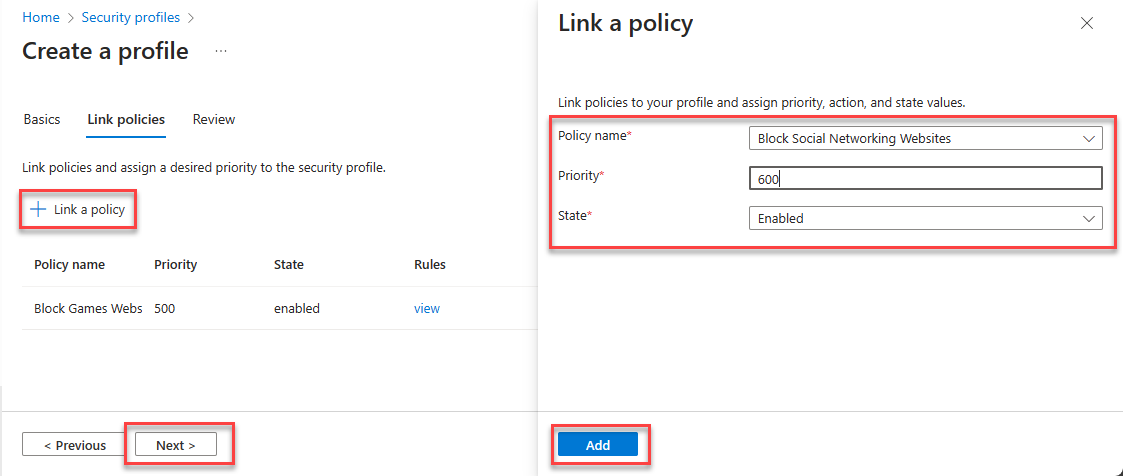
- Select Link a policy then Existing policy
- Select Policy name
- Enter Priority
- Select State as Enabled
- Click on Add then Next
- Review the linked policies and click on Create a profile
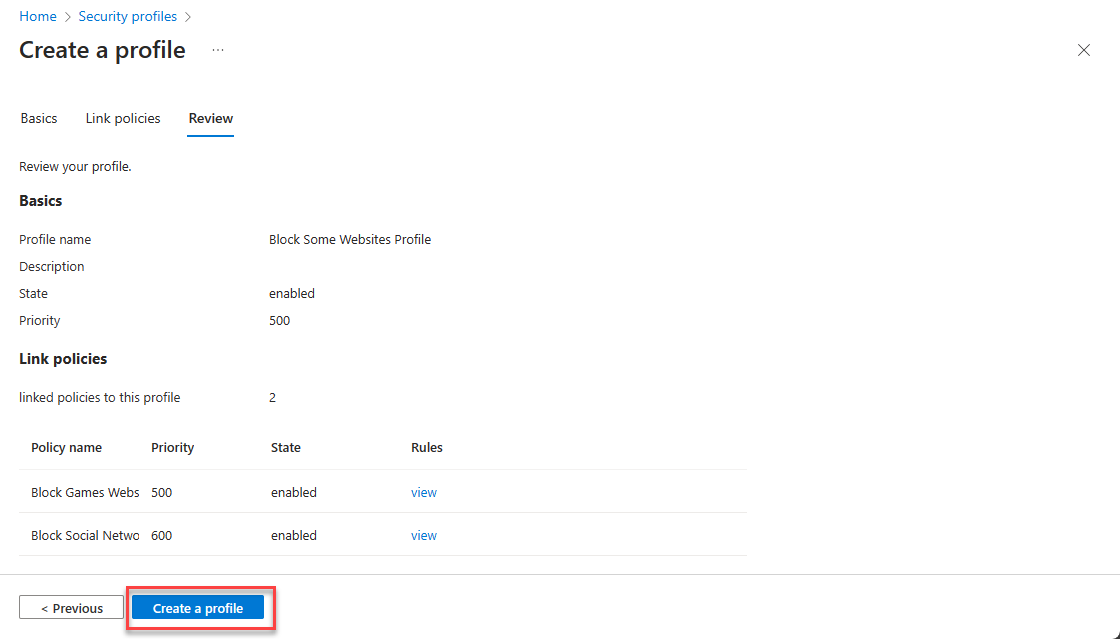
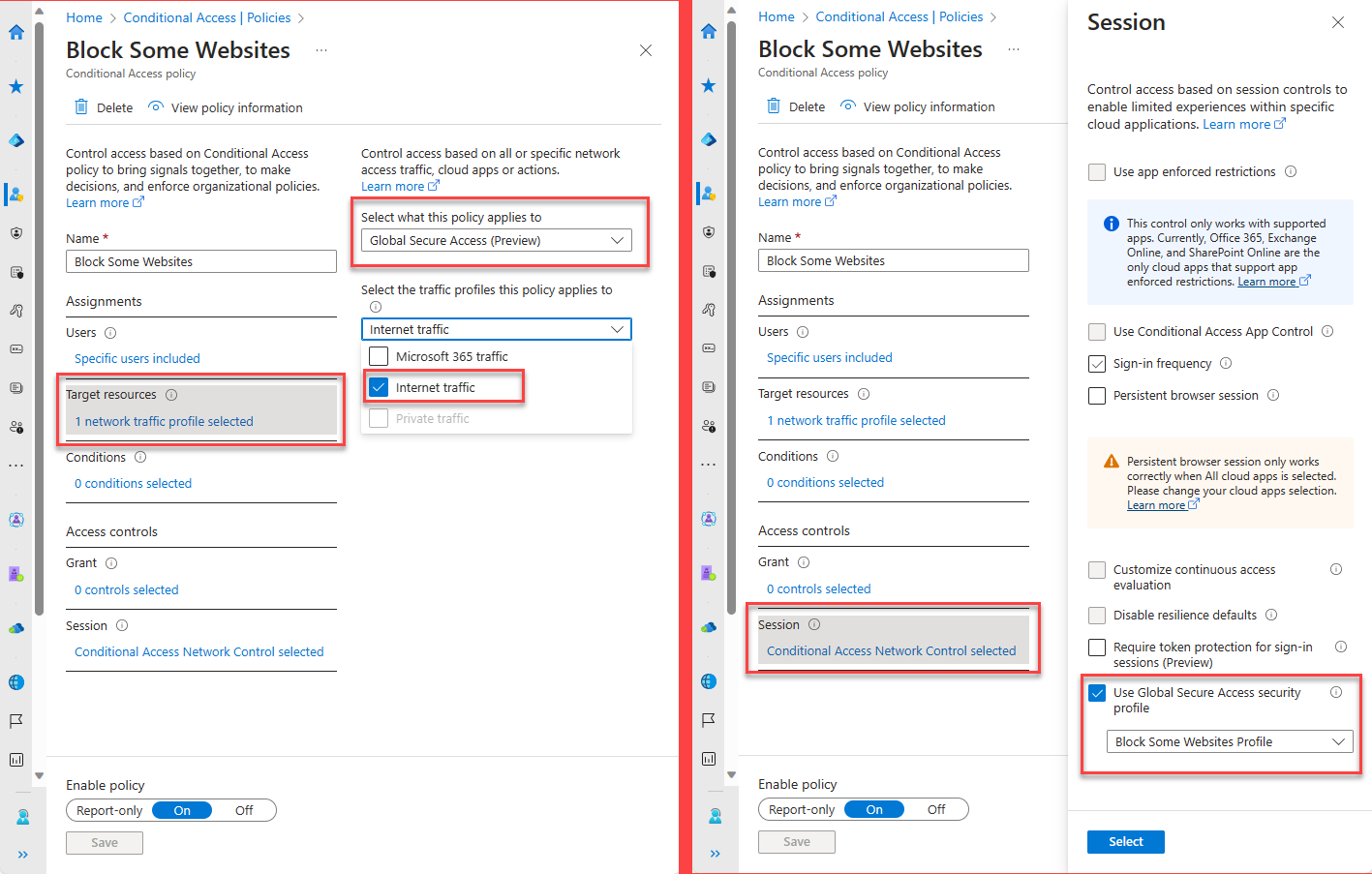
Create and Assign Conditional Access Policy
Navigate to Protection -> Conditional Access -> Create new policy.
- Select users and groups to assign the policy
- Select target resources as Global Secure Access then Internet traffic
- In Access Session controls, Select "Use Global Secure Access security profile" and assign priveoulsy created security profile
- Enable policy and Create
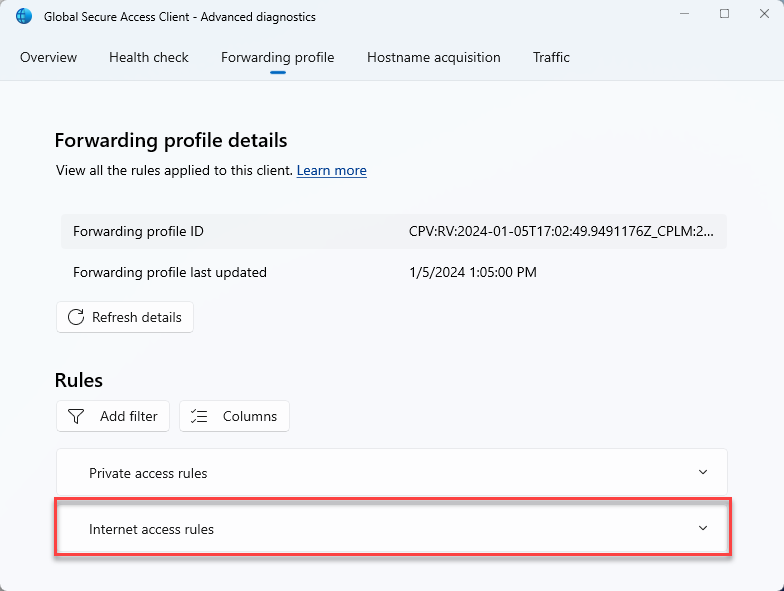
Verify Internet Access Rules
Login to the Microsoft Entra joined device where Global Secure Access client is installed.
Open Global Secure Access Client - Advanced diagnostics. Click on Forwarding profile and verify Internet access rules are available.
Demo
Verify Logs
Global Secure Access Client - Advanced Diagnostics
Open Global Secure Access Client - Advanced Diagnostics -> Traffic. Click on Start Collecting.
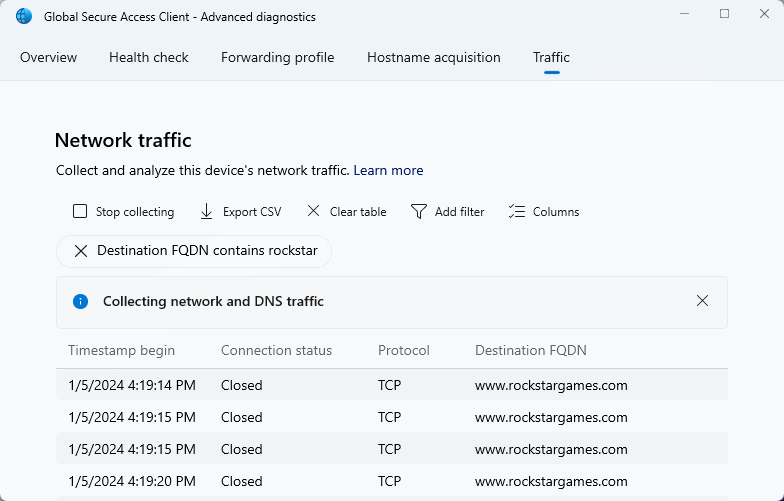
Entra Admin Center Traffic Logs
Navigate to Global Secure Access -> Monitor -> Traffic logs. Select Internet Access Connections
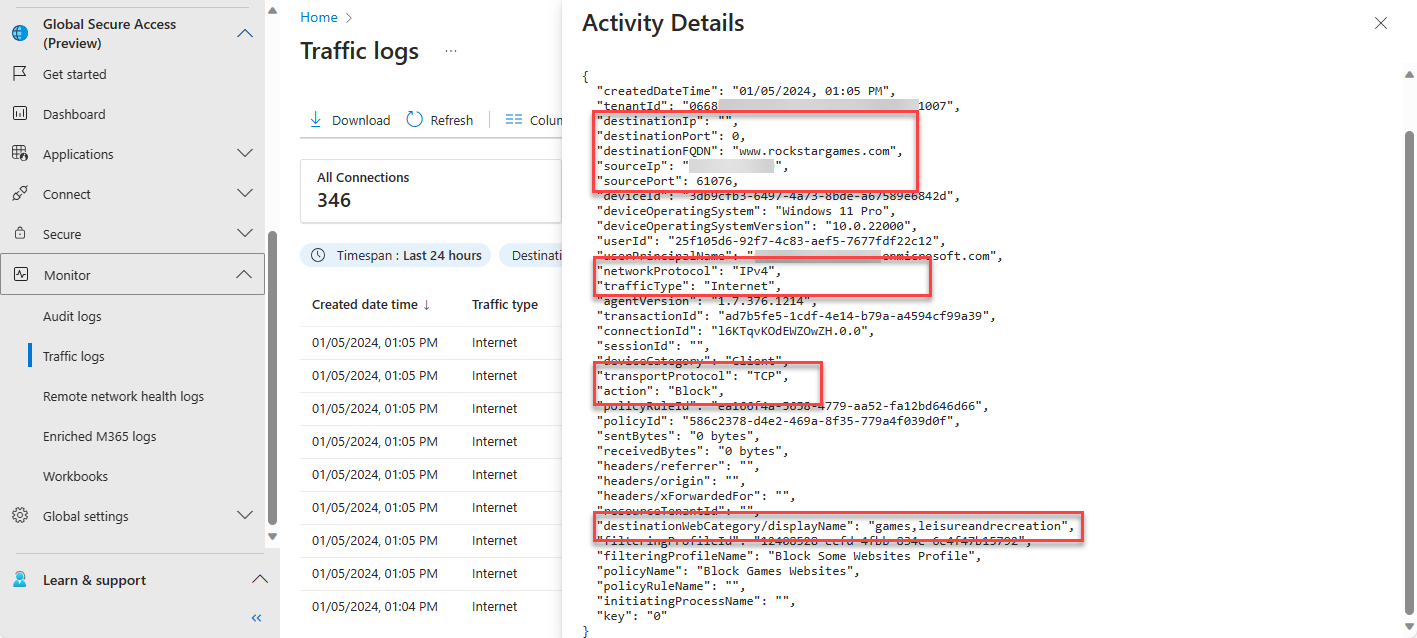
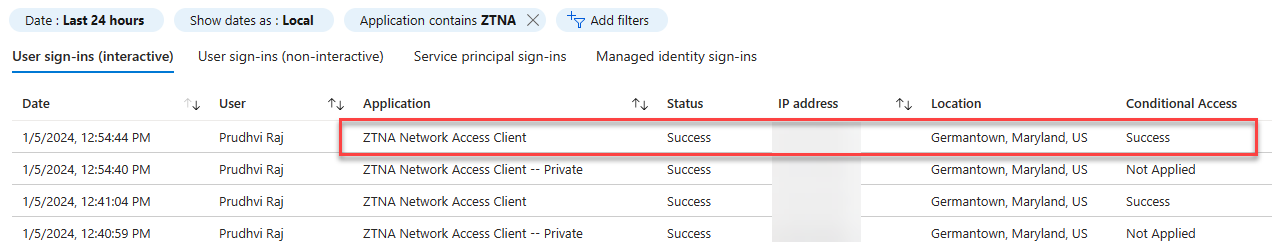
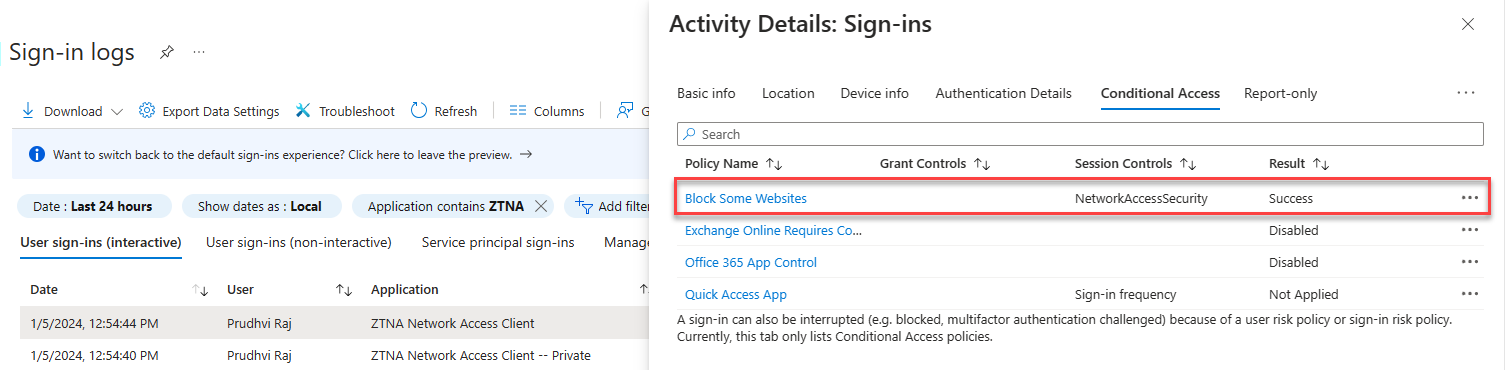
Conditional Access Sign-in Logs
Navigate to Protection -> Conditional Access -> Sign-in logs.