Entra Internet Access for Microsoft 365: Secure Microsoft 365 Traffic

In this article, will walk you through to configure Microsoft Entra Internet Access for Microsoft 365 to secure Microsoft 365 traffic through Global Secure Access client and Conditional Access.
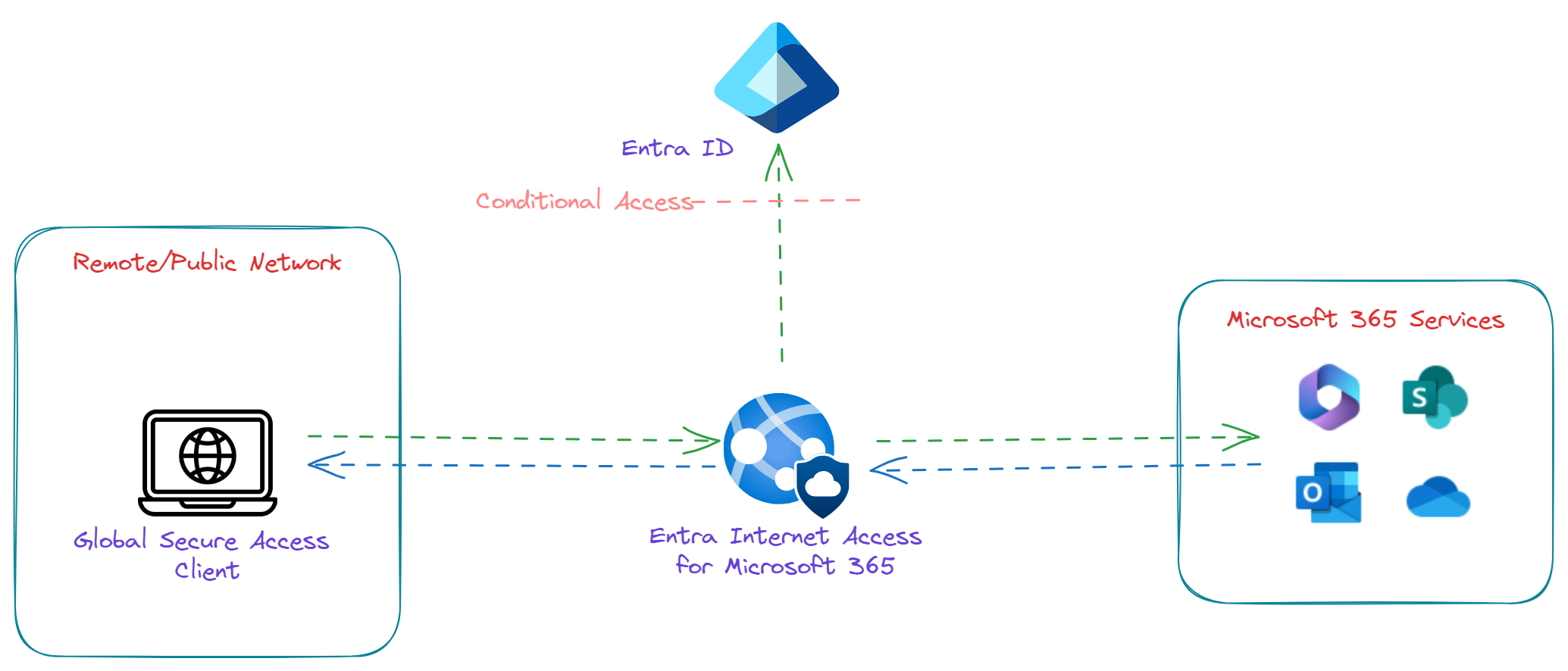
Microsoft Entra Internet Access provides an identity centric Secure Web Gateway (SWG) solution for SaaS applications and other internet resources by protecting users, devices and data from internet's wide threat landscape with a Conditional Access and visibility through traffic logs.
With Microsoft Entra Internet Access for Microsoft 365 profile enabled, Global Secure Access client acquires and tunnel the traffic going to Microsoft 365 services. The Microsoft 365 profile manages the following policies:
- Exchange Online
- SharePoint Online and OneDrive for Business
- Microsoft 365 Common and Office Online (only Microsoft Entra ID and Microsoft Graph. Teams is currently not supported)
Prerequisites
Required Roles
- Global Secure Access Administrator role: Required to setup and manage Entra Private Access
- Conditional Access Administrator or Security Administrator role; Required to create and interact with Conditional Access policies
Supported Devices
- Windows 10/11 (Microsoft Entra Joined)
- Android
- MacOS (Early Access - Private Preview)
- iOS (Early Access - Private Preview)
Licensing
- Microsoft Entra ID P1 license for GSA preview
- Microsoft 365 E3 license is recommended for Microsoft 365 traffic forwarding profile
Enable Microsoft 365 Access Profile
Login to entra.microsoft.com, Navigate to Global Secure Access -> Connect -> Traffic forwarding then enable Microsoft 365 access profile.
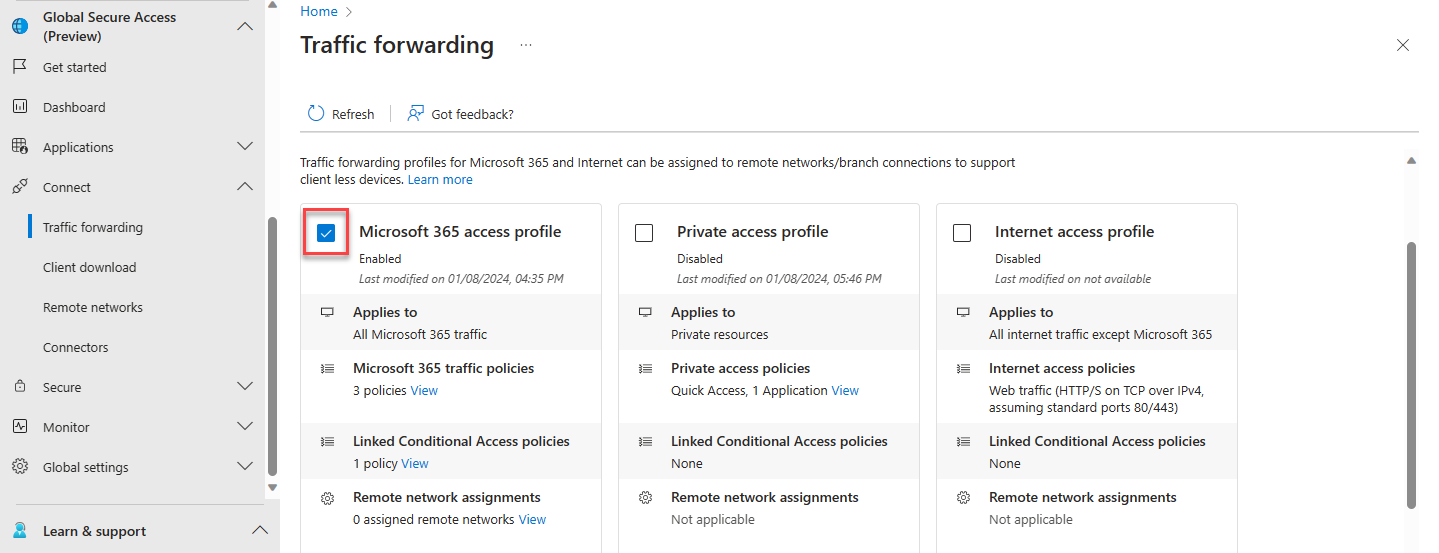
Manage Microsoft 365 Traffic Policies
To manage the Microsoft 365 traffic policies and rules, select the view link in Microsoft 365 traffic policies.
Use the check box to enable/disable the policy. Each policy comes with a range of rules with predefined the fqdn and IpSubnets. You can choose whether the traffic to forward or bypass.
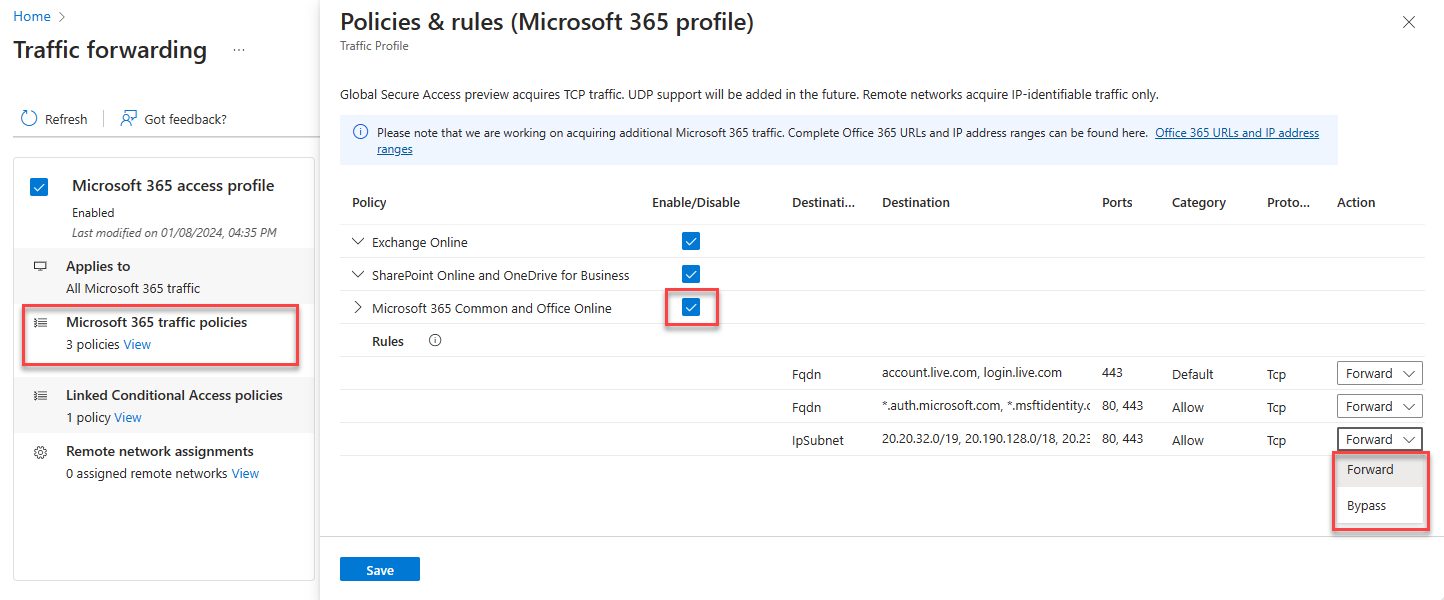
Microsoft 365 traffic will be forwarded through Global Secure Access service. If Global Secure Access client is unable to connect to GSA service, then traffic will bypass the service and sent directly to Microsoft 365 services instead of being blocked.
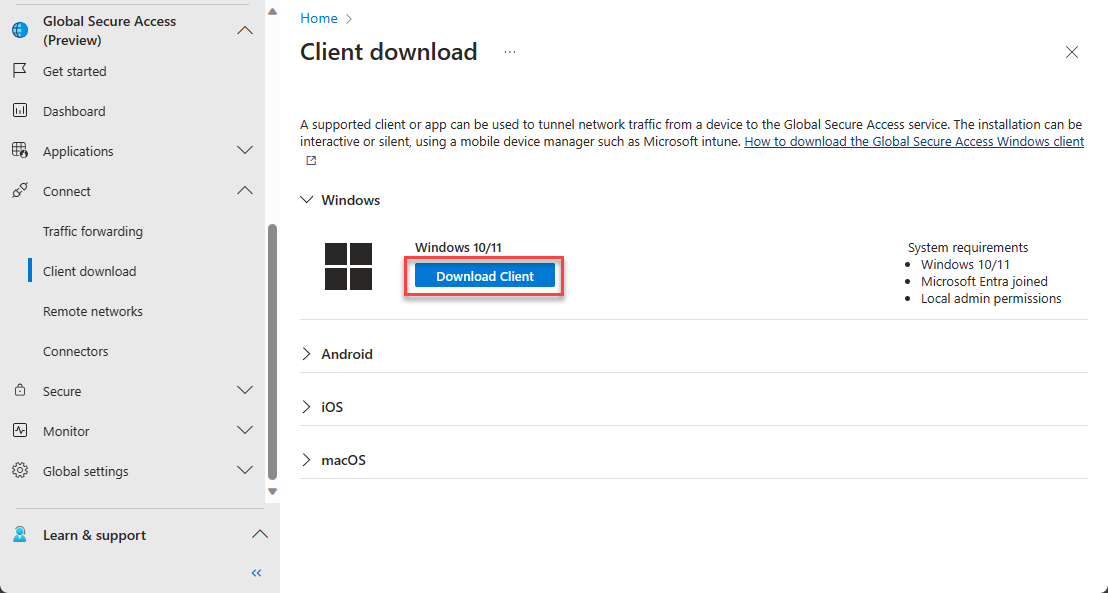
Download and Install Global Secure Access Client
Download the client from Global Secure Access -> Connect -> Client download page.
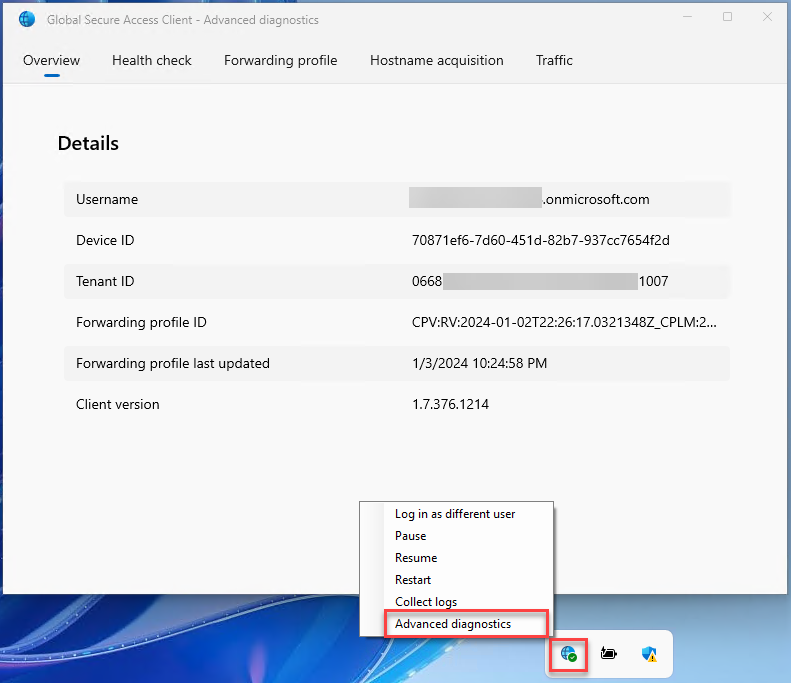
Install GSA client on a Entra joined Windows 10/11 device. Once installed, verify the service is running by opening the Advanced diagnostics and see the Overview and Health check.
Use Case Scenario
Foward the Microsoft 365 traffic through Global Secure Access service. If GSA client is unable to connect to service or not installed on a device, block the traffic from all locations except compliant network locations.
To achieve this use case, create following conditional access policies:
- Block access from any location except compliant network locations
- Grant access to Microsoft 365 traffic on Global Secure Access
Create and Assign Conditional Access Policy
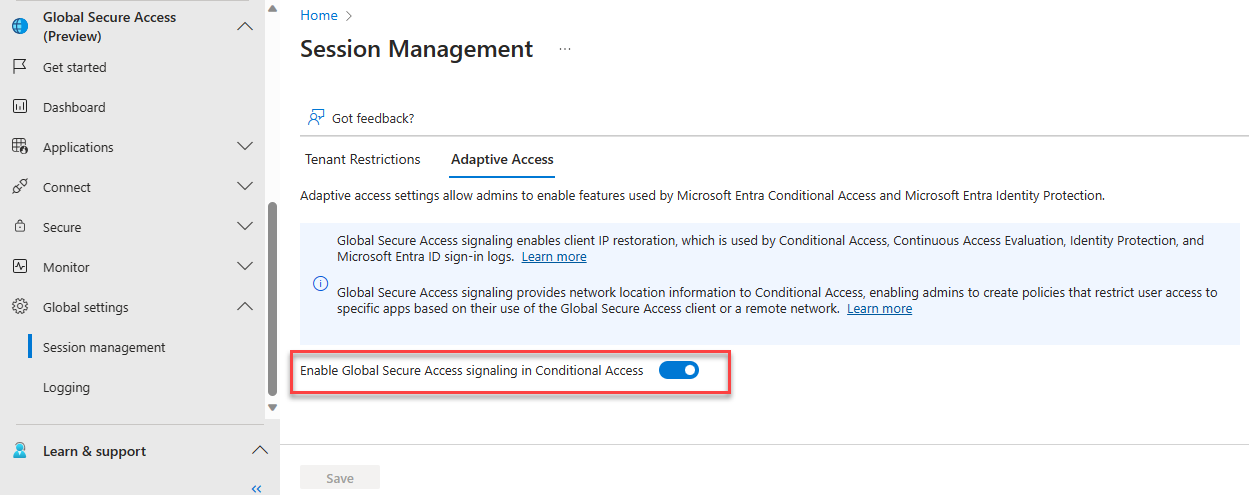
Before you assign a Conditional Access policy, make sure Adaptive Access is enabled.
Navigate to Global Secure Access -> Global Settings -> Session management -> Adaptive Access. Enable Global Secure Access signaling in Conditional Access.
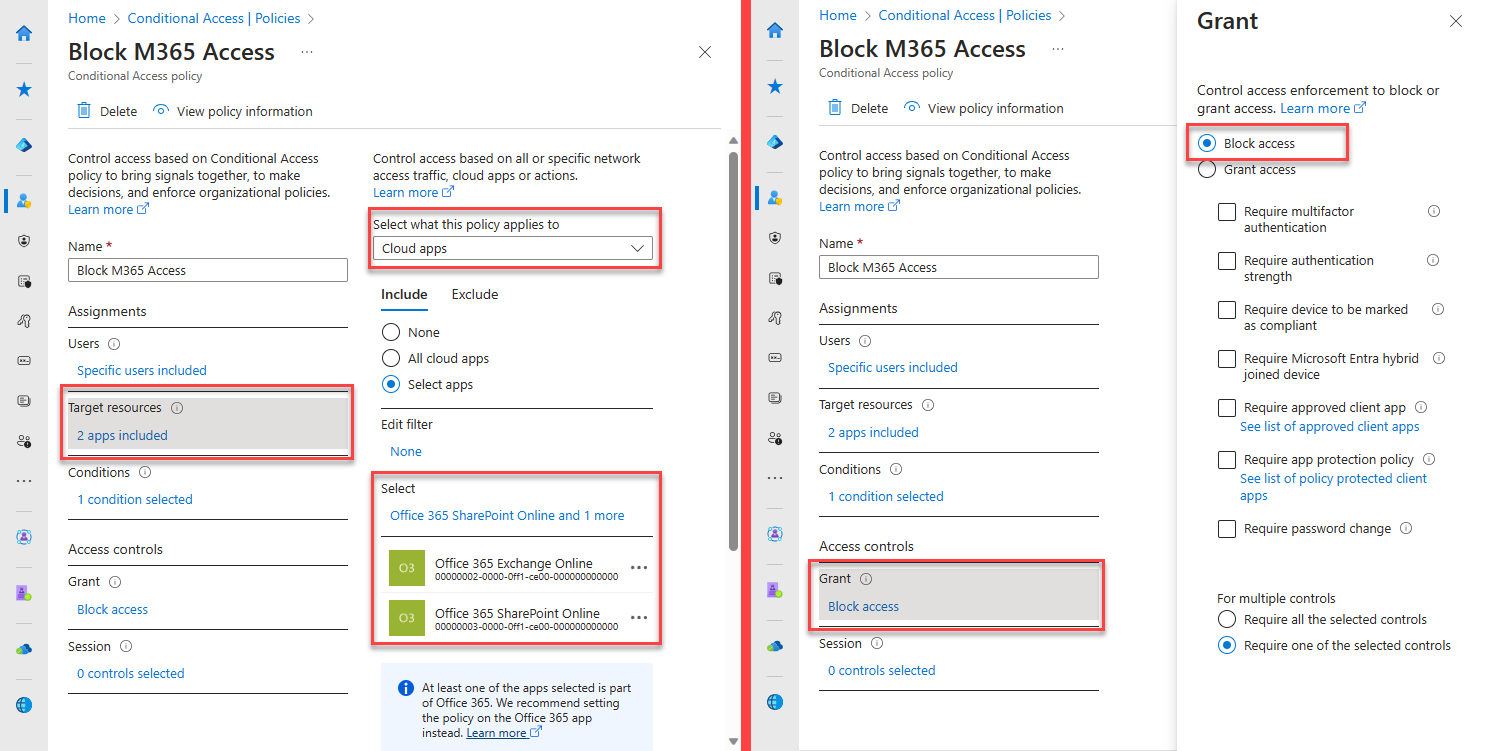
Navigate to Protection -> Conditional Access -> Create new policy.
To block access from any location except compliant network locations
- Select users and groups to assign the policy
- Select target resources as Cloud apps -> Selects apps then search and select Office 365 Exchange Online and Office 365 SharePoint Online
- In Access Grant controls, select Block access
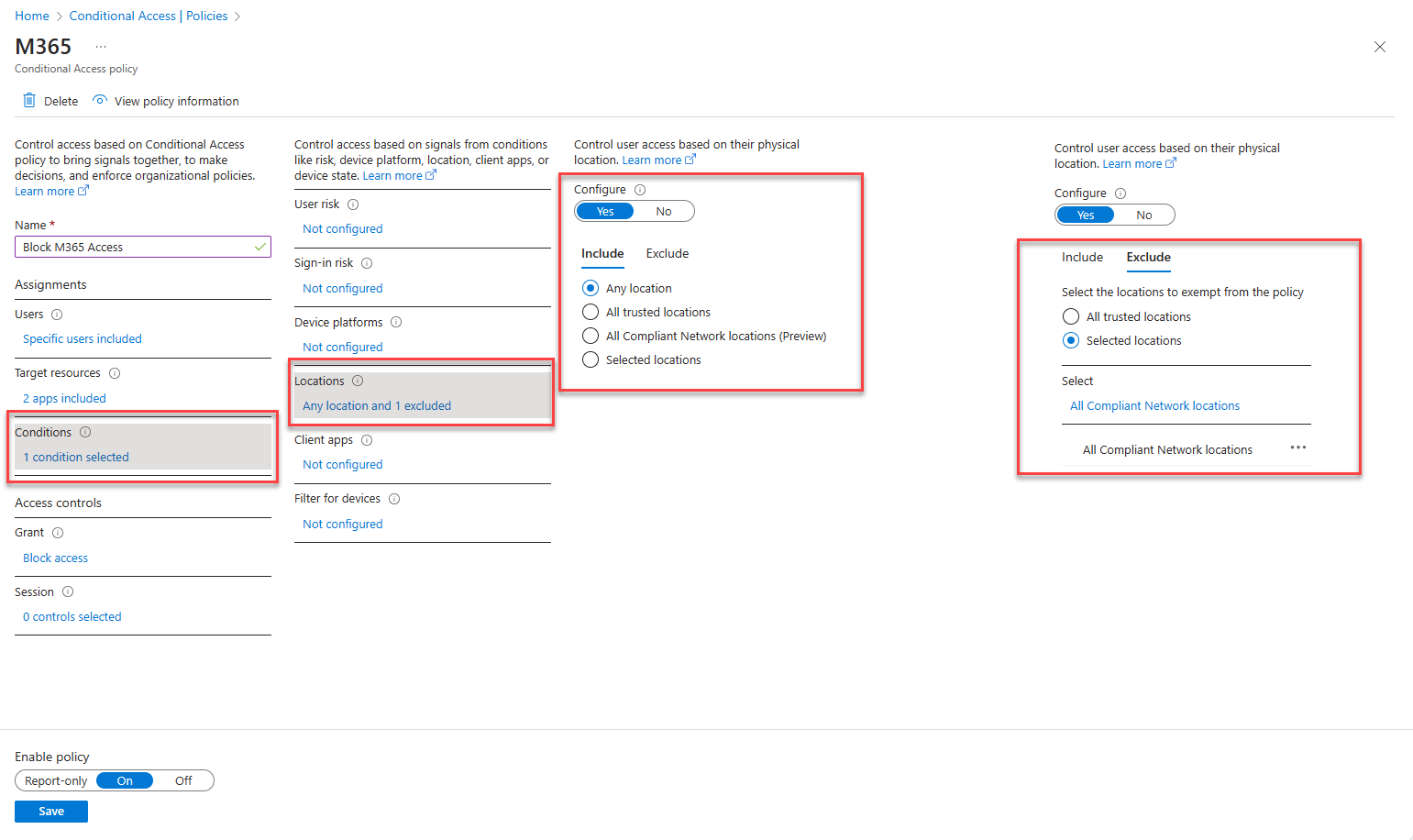
- Select Conditions -> Locations -> Configure to Yes
- Include: All locations
- Exclude: Selected locations -> All Compliant Network locations
- Enable policy and Create
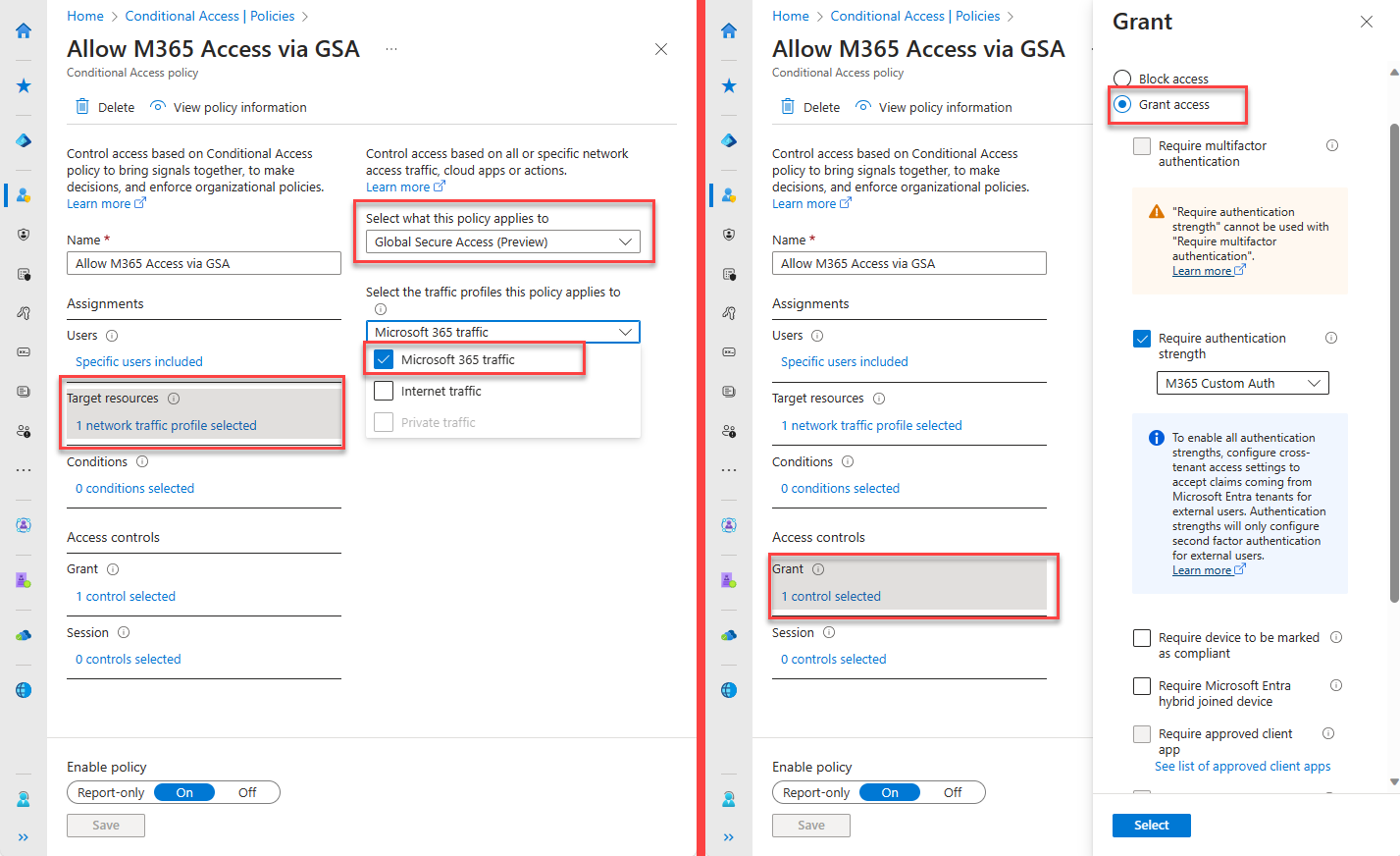
To grant access to Microsoft 365 traffic on Global Secure Access Service
- Select users and groups to assign the policy
- Select target resources as Global Secure Access then Microsoft 365 traffic
- In Access Session controls, Select "Use Global Secure Access security profile" and assign priveoulsy created security profile
- In Access Grant controls, select Grant access then select access controls as needed (in this case, Authentication strength selected)
- Enable policy and Create
Verify Microsoft 365 Access Profile Rules
Login to the Microsoft Entra joined device where Global Secure Access client is installed.
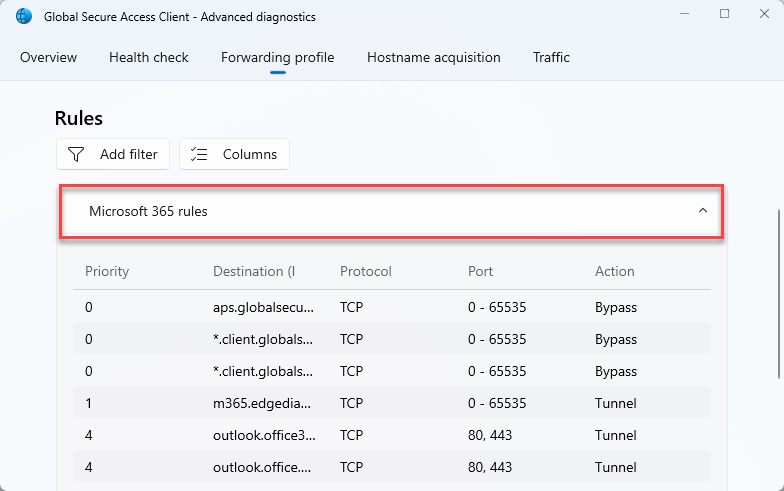
Open Global Secure Access Client - Advanced diagnostics. Click on Forwarding profile and verify Microsoft 365 rules are available.
Demo
Verify Logs
Global Secure Access Client - Advanced Diagnostics
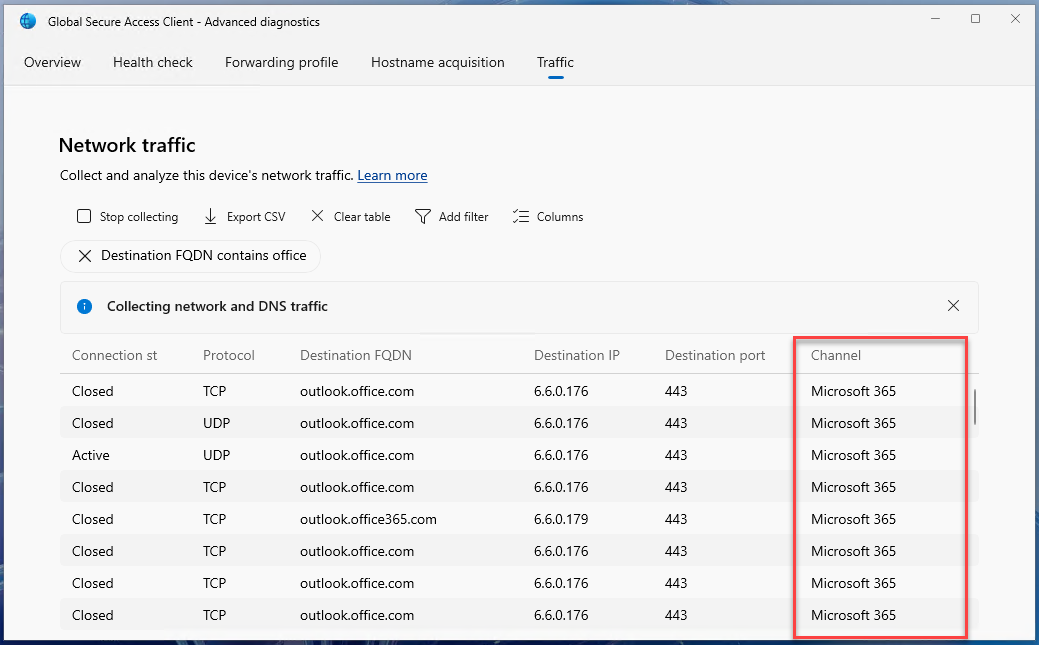
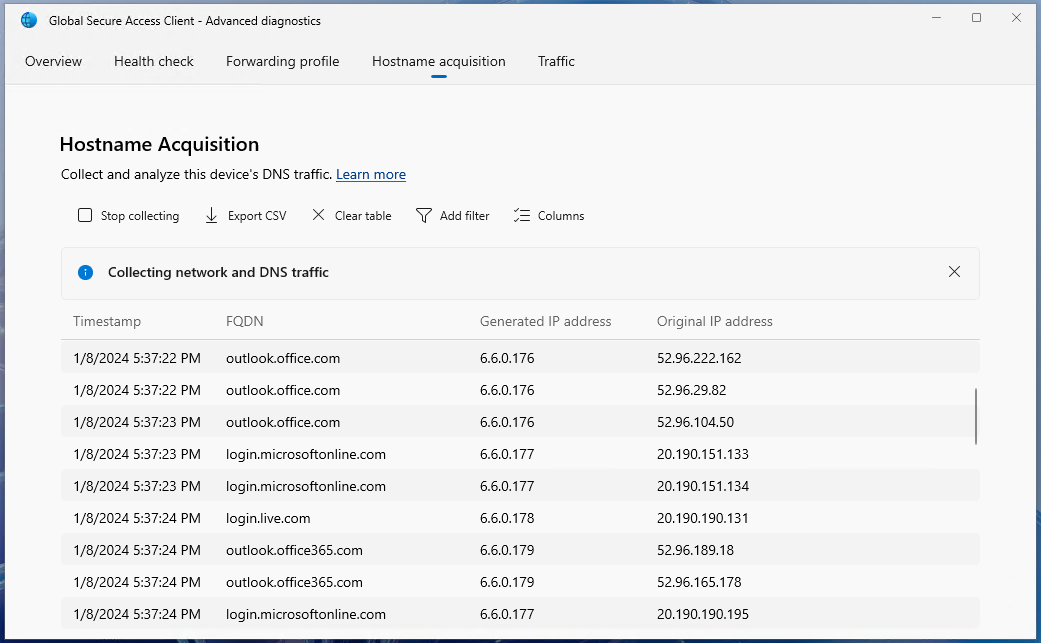
Open Global Secure Access Client - Advanced Diagnostics -> Traffic. Click on Start Collecting.
Entra Admin Center Traffic Logs
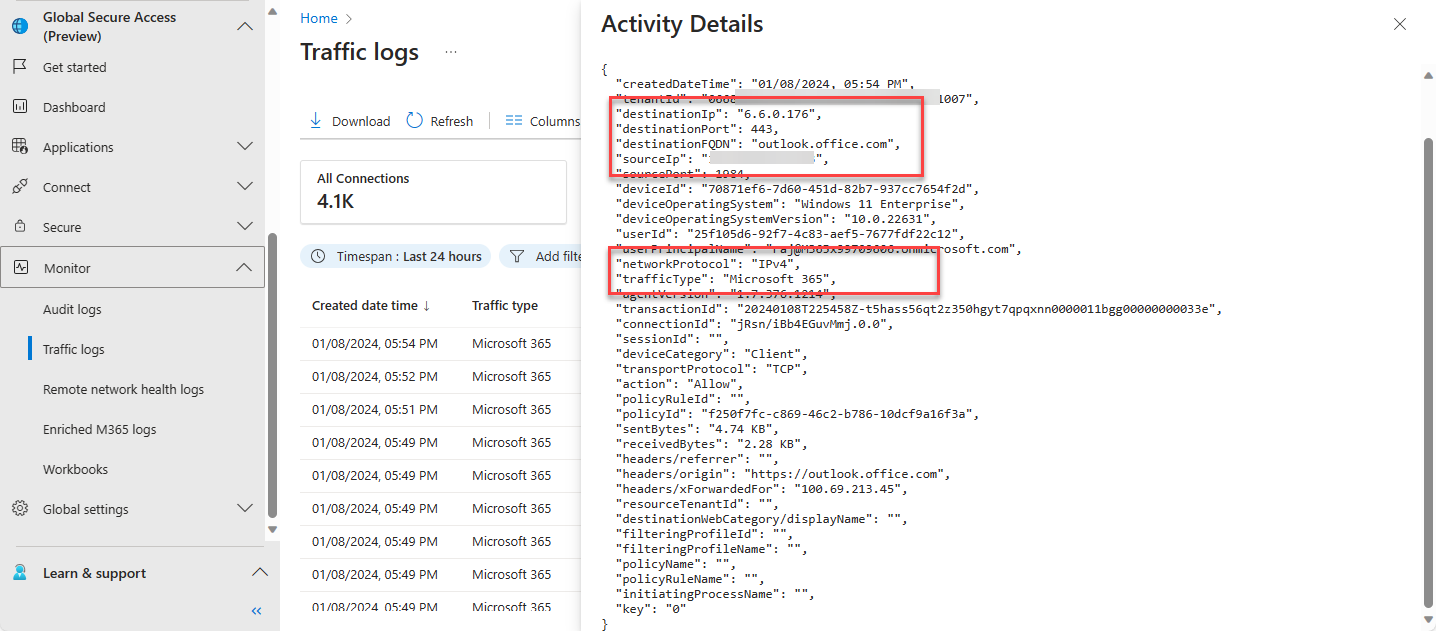
Navigate to Global Secure Access -> Monitor -> Traffic logs. Select Microsoft 365 Access Connections
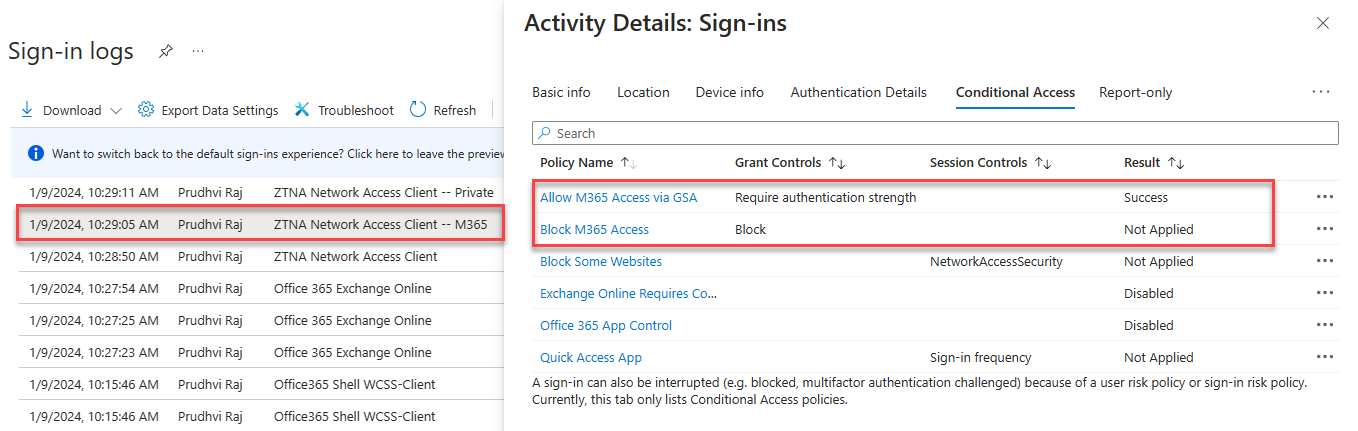
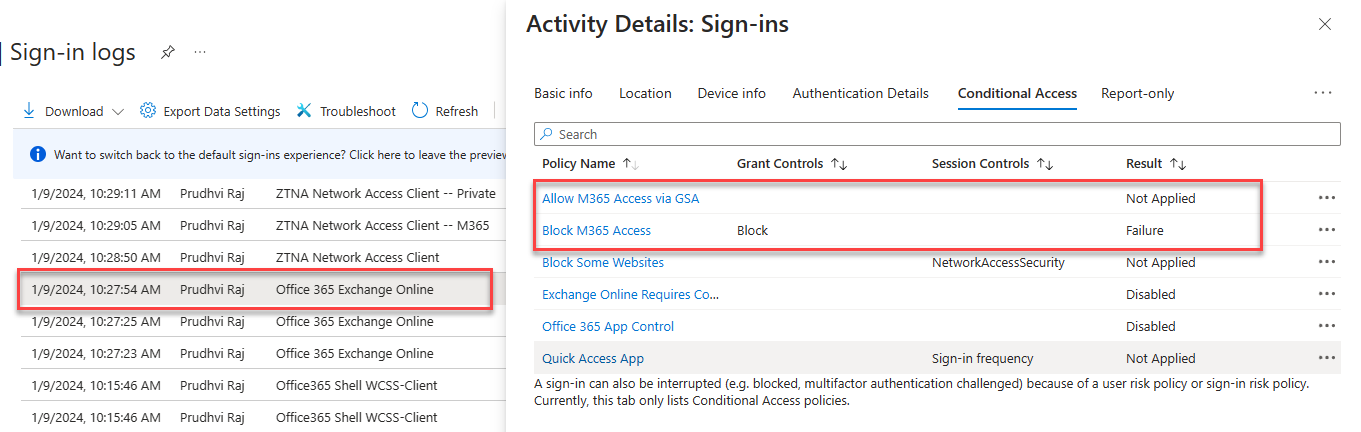
Conditional Access Sign-in Logs
Navigate to Protection -> Conditional Access -> Sign-in logs.