Enable OIDC Authentication in CyberArk PVWA with Microsoft Entra ID

In this tutorial, will demonstrate how to setup OIDC authentication in CyberArk PVWA with Microsoft Entra ID.
OIDC authentication enables users to authenticate to CyberArk PVWA using a single sign-on account through your organization's OIDC provider. CyberArk PVWA allows you to configure OIDC authentication for a single provider or for multiple providers.
Any user can use OIDC authentication method, whether user is created manually as CyberArk user or provisioned using LDAP integration. OIDC only handles authentication. This means that user provisioning, authorization and LDAP group membership should be configured in CyberArk's user management or through LDAP mapping.
Create App Registration in Microsoft Entra ID
Login to entra.microsoft.com, Navigate to Identity -> Applications -> App registrations, then click on New registration.
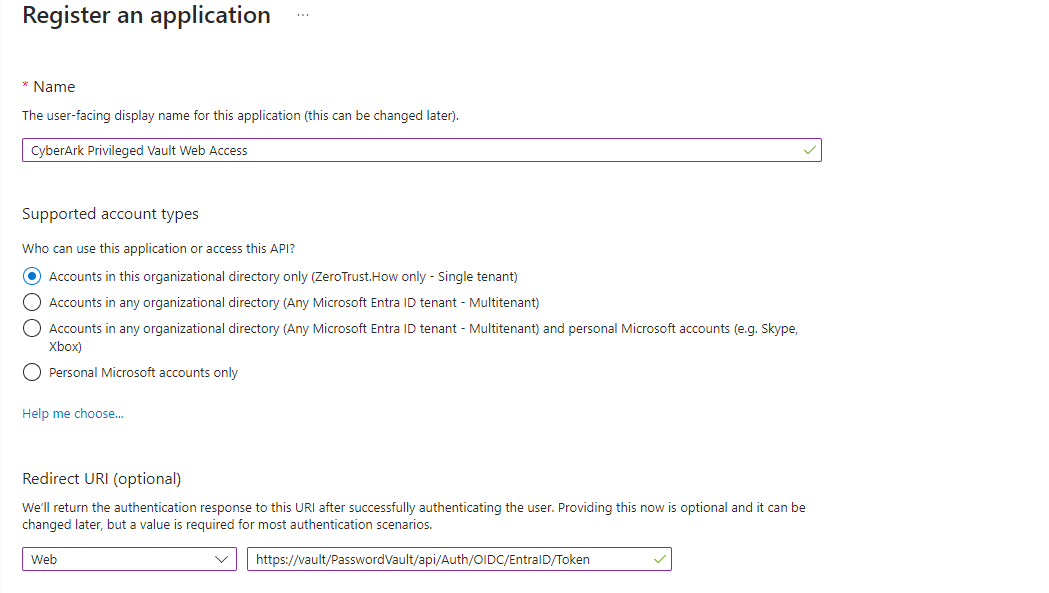
In the Register an application form, enter details as follows:
Name: CyberArk Privileged Vault Web Access
Supported account types: Accounts in this organizational directory only
Redirect URI: Web
Redirect URI value: https://<pvwa-dns>PasswordVault/api/Auth/OIDC/<oidc-provider-id-in-pvwa>/Token
Click on Register.
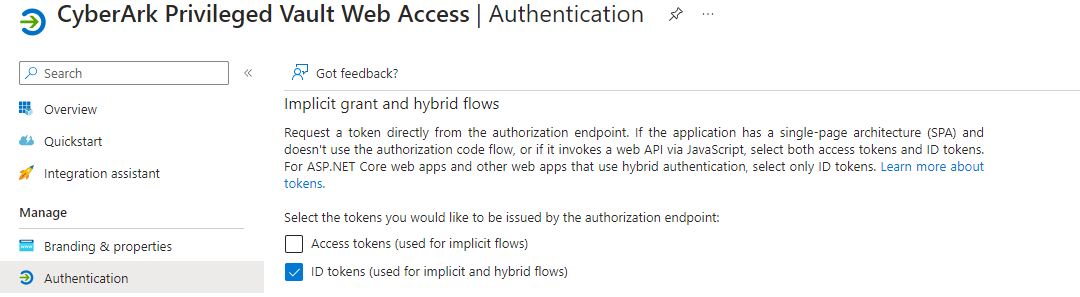
Navigate to Authentication and enable ID tokens.
Navigate to Certificates and secrets, Generate a new client secret. Keep a note of client secret before you leave this screen.
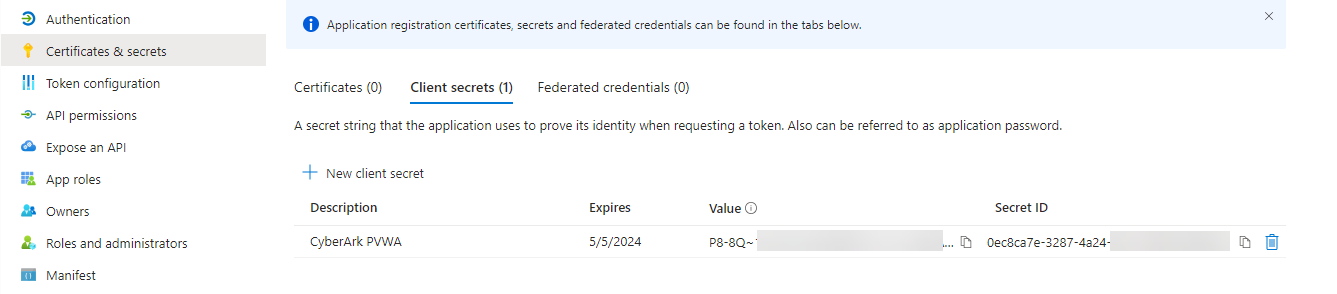
Navigate to Manifest and change value of acceptMappedClaims to true.
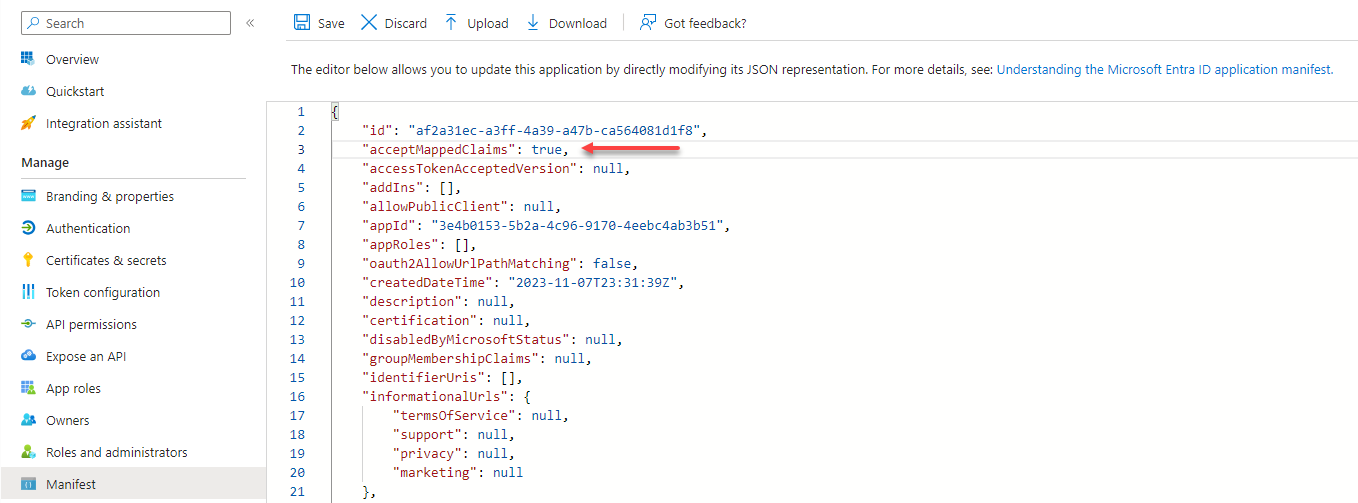
Navigate to Overview and open Managed application.
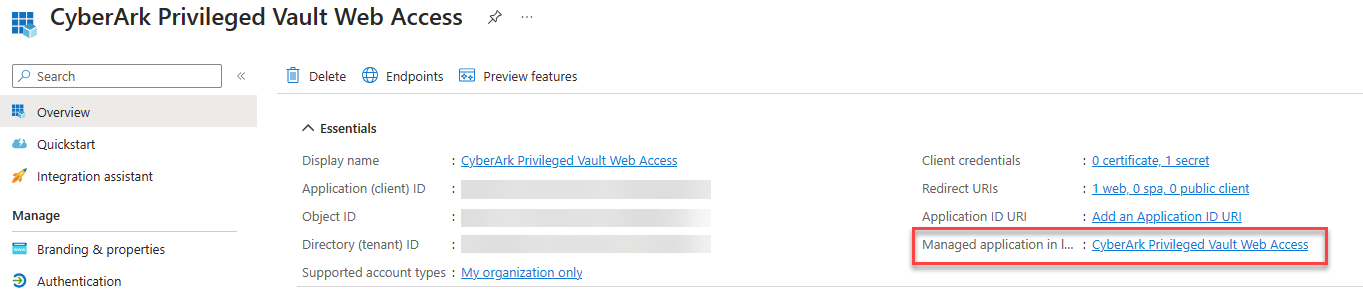
Go to Single sign-on, click on edit in Attributes and Claims.
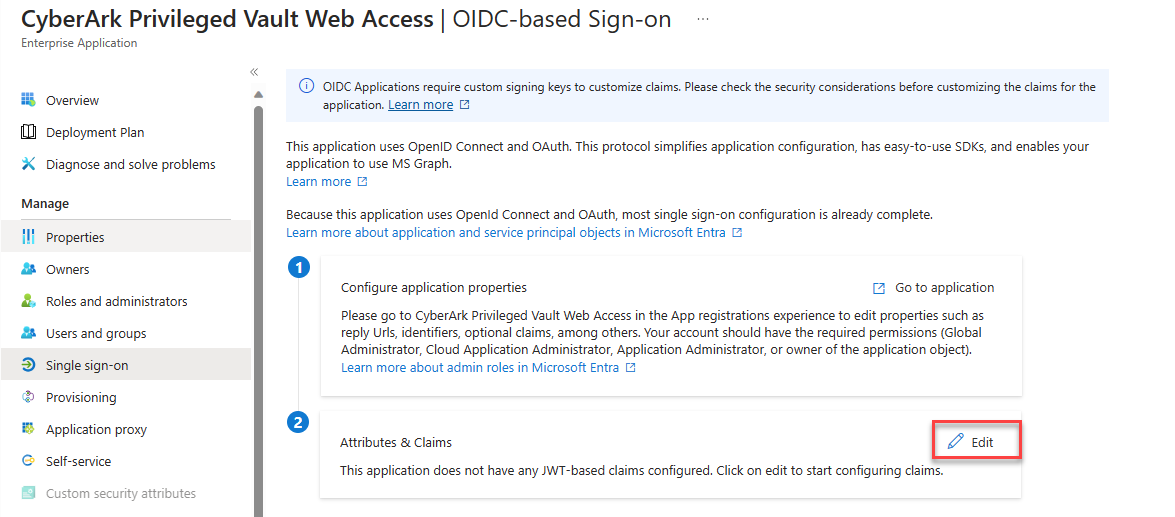
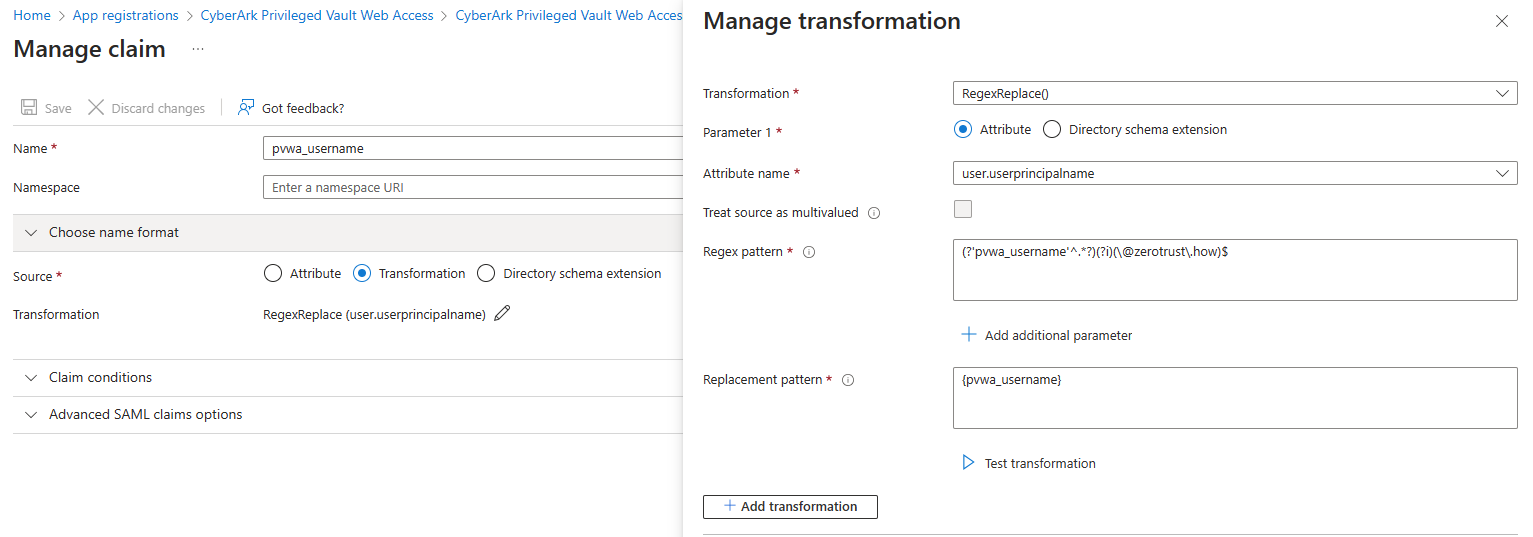
Transform any existing claim into a new claim to match its value with the CyberArk Vault/LDAP username.
In this case, Entra ID's userprincipalname is pamadmin01@zerotrust.how and CyberArk Vault username is pamadmin01. Use claim transformation to transform userprincipalname claim into new claim named pvwa_username.
Click on Add new claim and provide the values as follows:
Name: pvwa_username
Source: Transformation
Transformation: RegexReplace()
Attribute name: user.userprincipalname
Regex pattern: (?'pvwa_username'^.*?)(?i)(\@zerotrust\.how)$
Replacement pattern: {pvwa_username}
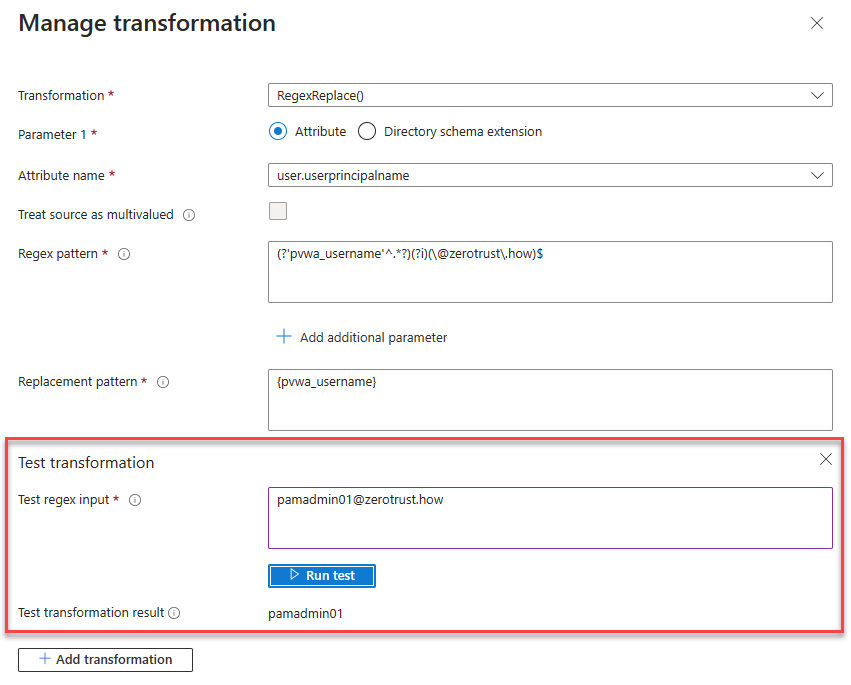
Test the claim transformation, to make sure you are receiving the desired value in new claim.
Make a note of following information from Entra ID App Registration before you proceed to CyberArk PVWA: App Client ID, App Client Secret and OpenID Connect metadata document URL ( https://login.microsoftonline.com/<tenant-id>/v2.0/.well-known/openid-configuration ).
Create OIDC Authentication Method in CyberArk PVWA
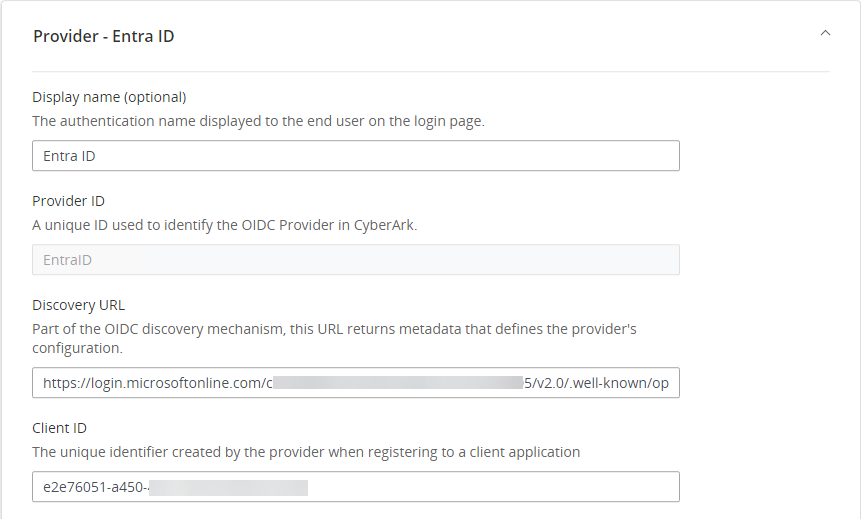
Log in to CyberArk PVWA and Navigate to Administration -> OIDC authentication. Enter the provider information as follows:
Display name: name to display to the end user on login page (Entra ID)
Provider ID: unique id to identify the OIDC provider in CyberArk PVWA (EntraID)
Discovery URL: OpeID Connet metadata document URL
Client ID: App Client ID
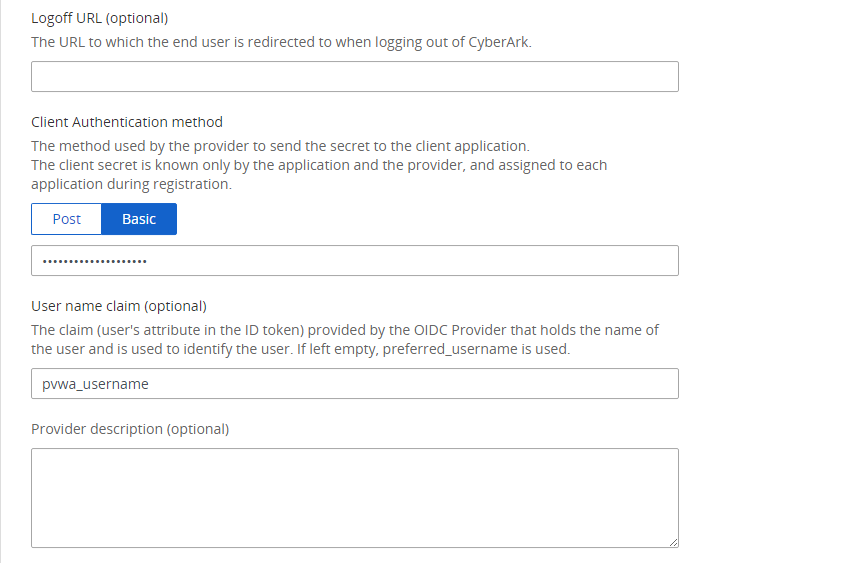
Client Authentication method: Basic and App Client Secret
Username claim: Claim name provided by the OIDC provider to identiy user. Default preferred_username. In this case, pvwa_username.
Enable OpenID Provider and click Save.
To define Provider's URL in the Allowed Referrer list in the Access Restriction Settings
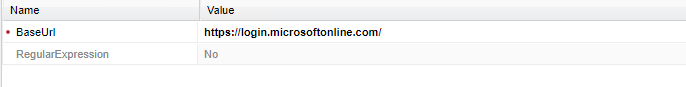
Navigate to Administration -> Configuration Options -> Options. Right click Access Restriction and select Add AllowedReferrer.
Enter Microsoft Entra ID's base URL in BaseUrl field.
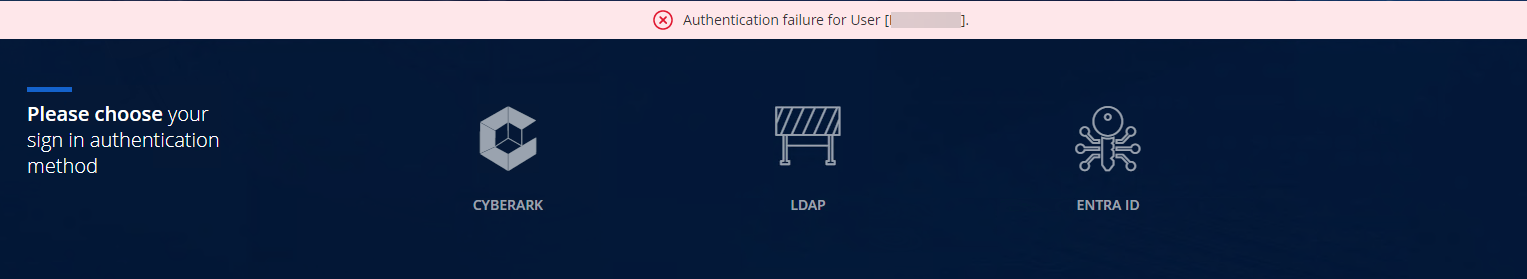
Once OpenID provider is enabled, it will be available in the logon page for user to authenticate to CyberArk PVWA.


User successfully authenticated with OIDC provider but doesn't have an account in CyberArk PAS. User will be presented with authentication failure error.