What is Microsoft Entra Permissions Management?
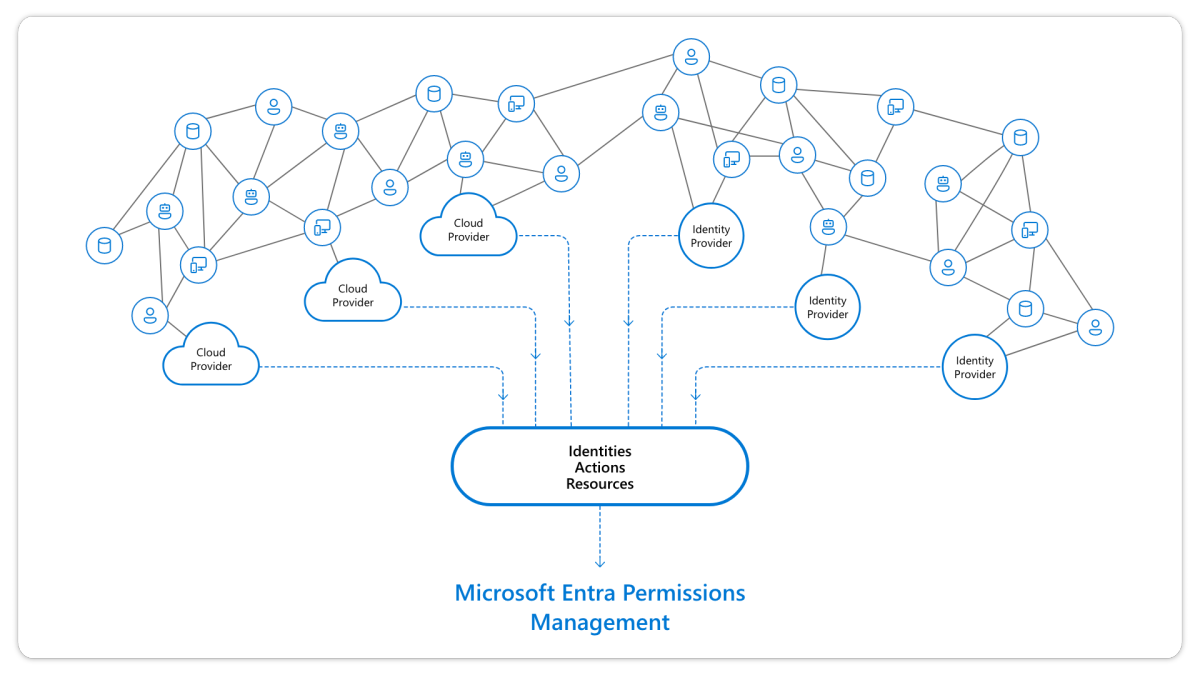
Microsoft Entra Permissions Management (EPM) is a cloud infrastructure entitlement management (CIEM) solution that provides comprehensive visibility into permissions assigned to all identities such as user identities, workload identities, actions and resources across multi-cloud infrastructures.
As of today, Entra Permissions Management supports all three major cloud providers: Microsoft Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP).
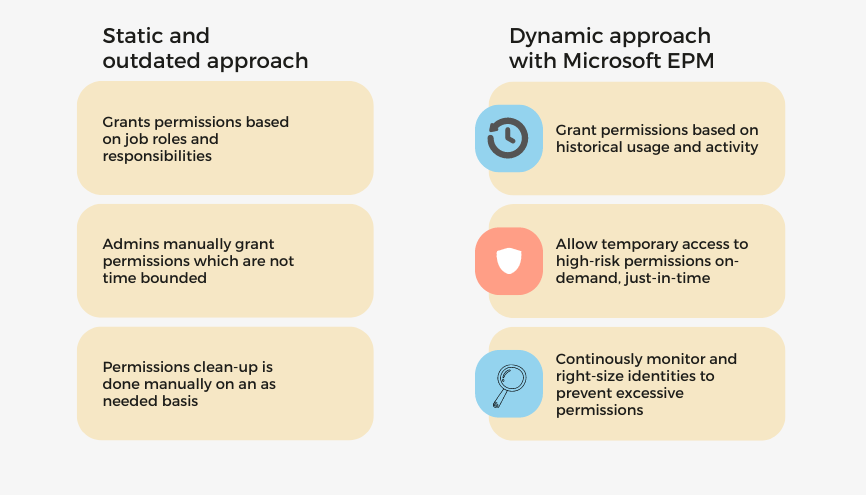
Microsoft EPM detects, automatically right-sizes, and continuously monitors unused and excessive permissions. Microsoft EPM manages the permissions based on historical usage and activities.
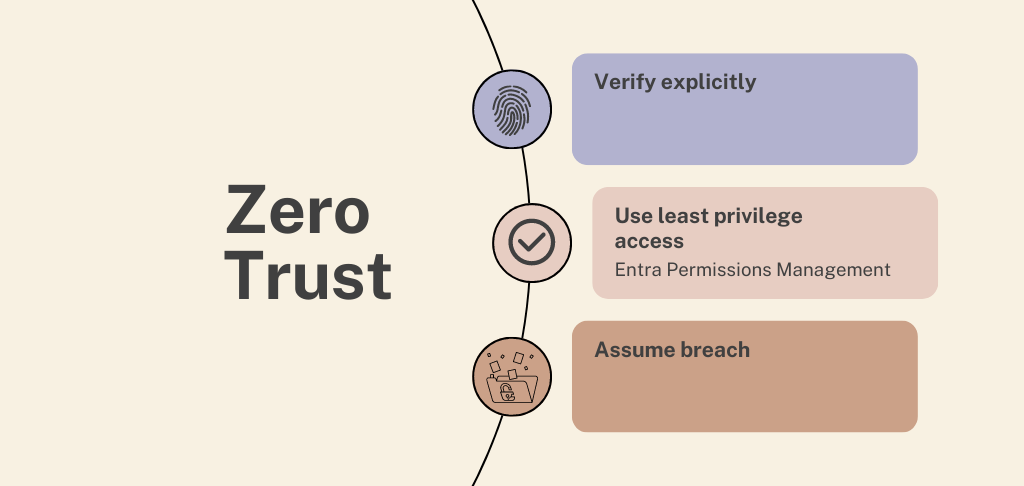
Where does Microsoft EPM fit in Zero Trust security?
EPM deepens Zero Trust security strategies by augmenting the least privilege access principle, allowing organizations to:
- Get comprehensive visibility: Discover which identity is doing what, where, and when.
- Automate least privilege access: Use access analytics to ensure identities have the right permissions, at the right time.
- Unify access policies: Implement consistent security policies across your cloud infrastructure.
Why organizations have to consider Microsoft EPM?
- Permissions Gap: Difference between the permissions that are granted to users, groups, workload identities and resources versus the permissions that they use.
- Complexity of Multi-Cloud: Inconsistency of cloud providers’ native access management models makes it even more complex for Security and Identity to manage permissions and enforce least privilege access policies.
- Orphaned Privileged Identities: Users that have left organization and still have their identities active or Users that are moved to different areas within an organization but retained their privilege access from previous assignment.
- Permissions Creep: Evaluate the permissions used by any identity over the time and develop a baseline of permissions needed.
- Self Service, Just-In-Time Access: Develop a mechanism where users can request time bound, just in time access to the elevate permissions.
- Identity Sprawl: Different types of identities such as native cloud users, directory synced users, external users, workload identities, etc.,
Key Phases of Microsoft EPM

Discover & Assess
- Permissions discovery across multi-cloud infrastructure AWS, Azure, and GCP.
- Periodically evaluates the level of risk associated with the number of unused or excessive permissions across your identities and resources. Provides an aggregated metric called Permission Creep Index (PCI).
- Multi-dimensional view of permissions risk for all identities, actions, and resources.
Remediate & Manage
- Right size the permissions based on historical usage and activities.
- Automated deletion of permissions unused for the past 90 days.
- Grant identities permissions on-demand for a time-limited period or an as-needed basis with an approval workflow.
Monitor & Alert
- ML-powered anomaly detections.
- Context-rich forensic reports around identities, actions, and resources to support rapid investigation and remediation.
- Autopilot Rules and recommendations to right sizing the permissions.
Finally, Microsoft Entra Permissions Management lets your organization implement one of the core pillars of a modern Zero Trust security with the following key capabilities:
- Cross-cloud visibility
- Automated remediation
- Anomaly detections and alerts
- Detailed forensic reports



