Enable OIDC Authentication in CyberArk PVWA with CyberArk Identity

n this tutorial, will demonstrate how to setup OIDC authentication in CyberArk PVWA with CyberArk Identity.
OIDC authentication enables users to authenticate to CyberArk PVWA using a single sign-on account through your organization's OIDC provider. CyberArk PVWA allows you to configure OIDC authentication for a single provider or for multiple providers.
Any user can use OIDC authentication method, whether user is created manually as CyberArk user or provisioned using LDAP integration. OIDC only handles authentication. This means that user provisioning, authorization and LDAP group membership should be configured in CyberArk's user management or through LDAP mapping.
Create Roles in CyberArk Identity
Log in to CyberArk Identity Admin Portal and Navigate to Core Services -> Roles menu, then click on Add Role button.
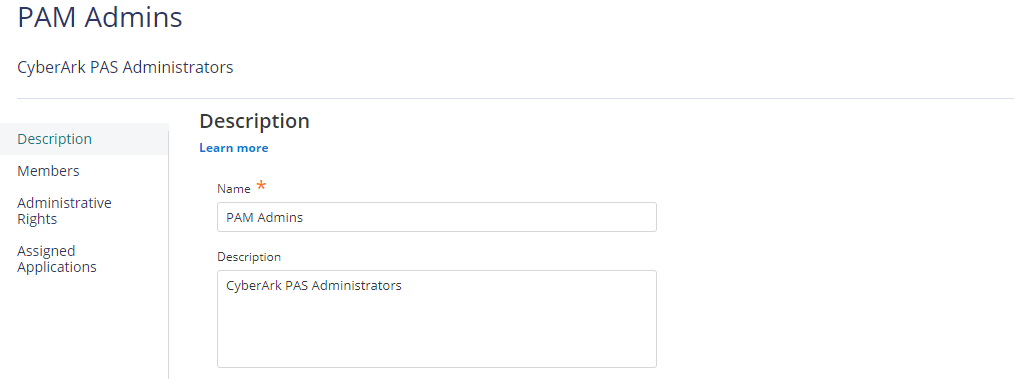
On the Add Role screen, Enter Role Name and Description (optional) then click on Save. In this case, I created a role named PAM Admins.
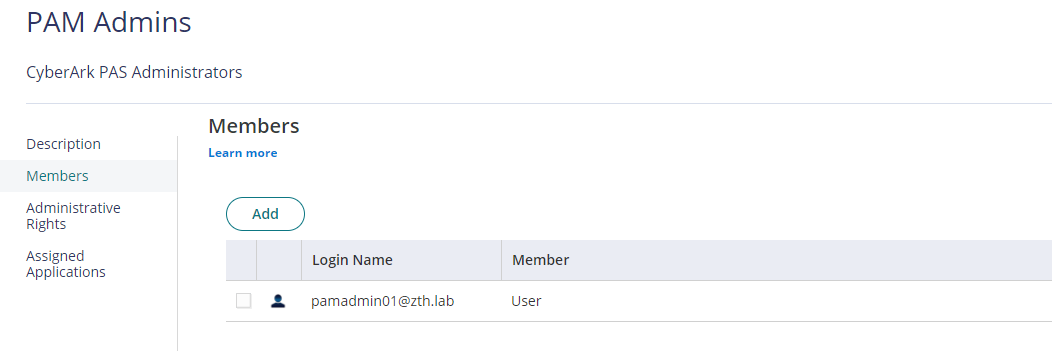
Click on Members tab of the Role, Add Users as needed, then click on Save.
Create a Web App in CyberArk Identity
Navigate to App & Widgets -> Web Apps menu, then click on Add Web Apps button.
On the Add Web Apps screen, choose Custom and click on Add button next to OpenID Connect. Click Yes on confirmation and click close.
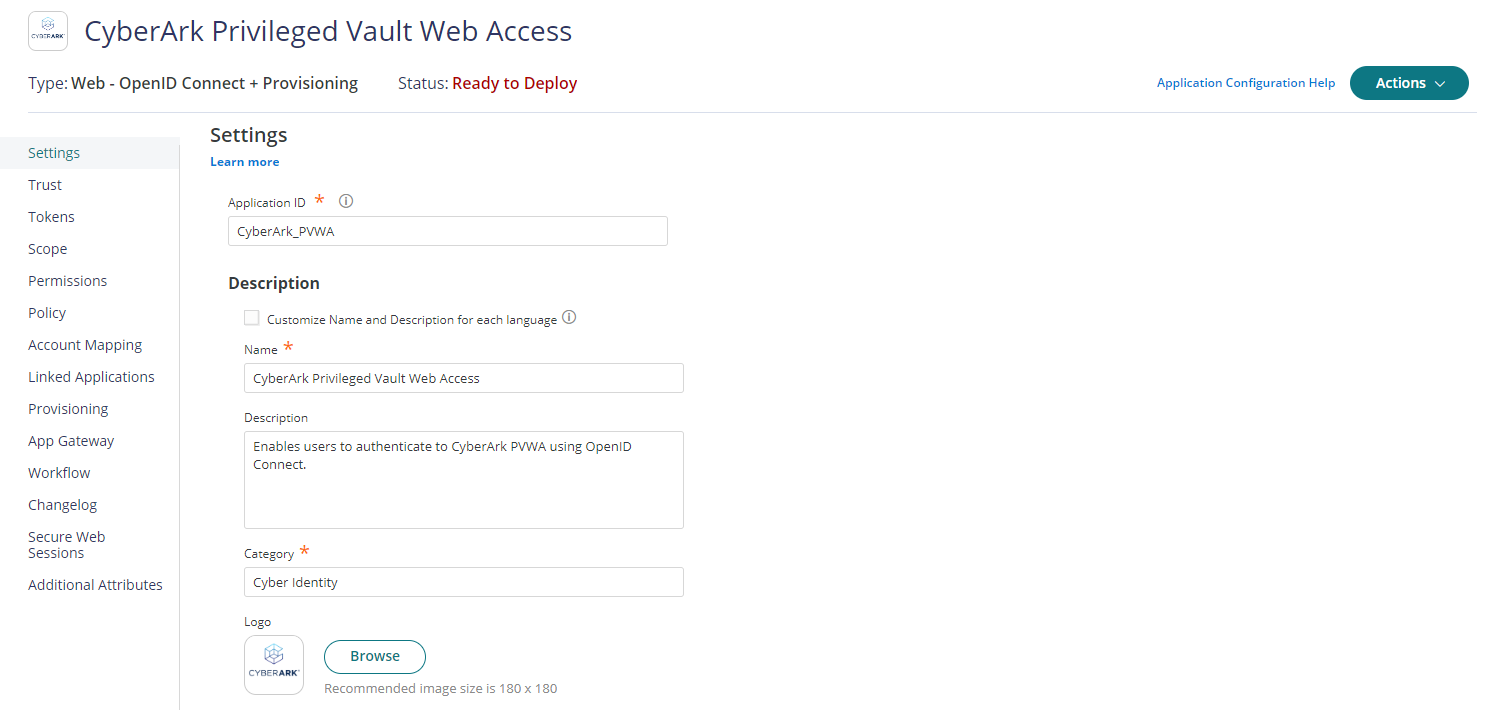
Once closed, page will be redirected to Settings tab of OIDC application.
In Settings tab, Provide the Application ID, value must be unique across your CyberArk Identity tenant. Enter Application Name and click on Save.
Click on Trust tab, Under Identity Provider Configuration, enter OpenID Connect client secret.
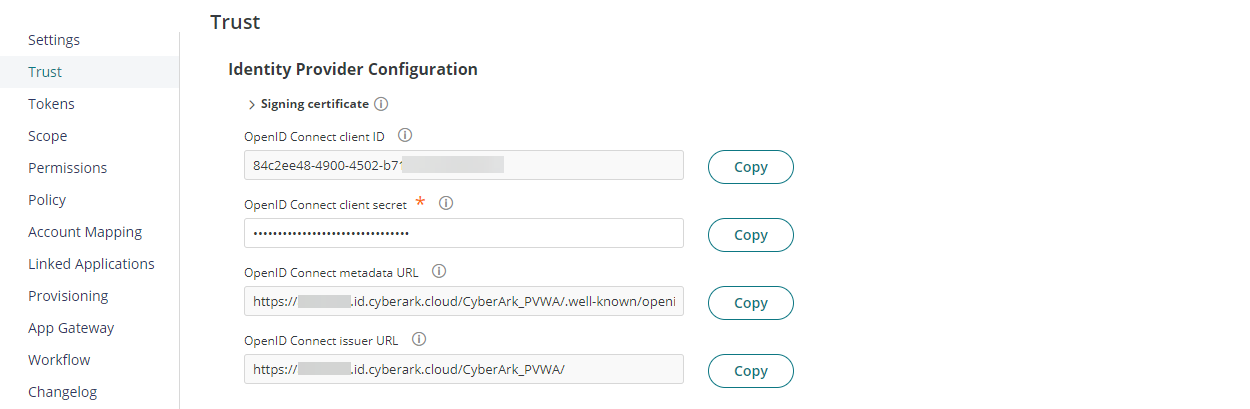
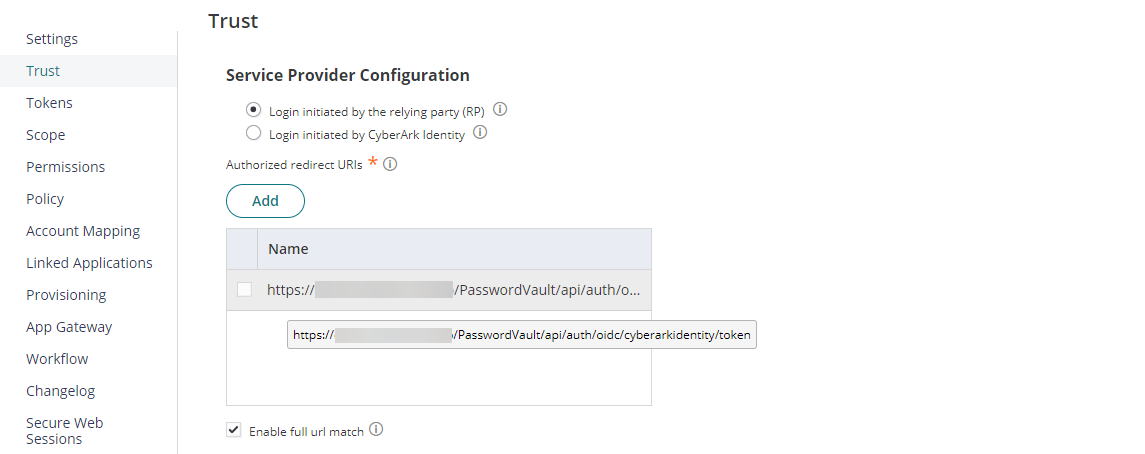
Under Service Provider Configuration, Select Login initiated by the relying party (RP). Add Authorized redirect URIs value to https://<pvwa-dns>/Passwordvault/api/auth/oidc/<oidc-provider-id-in-pvwa>/token then click Save. These URI values align with what the CyberArk PVWA expects.
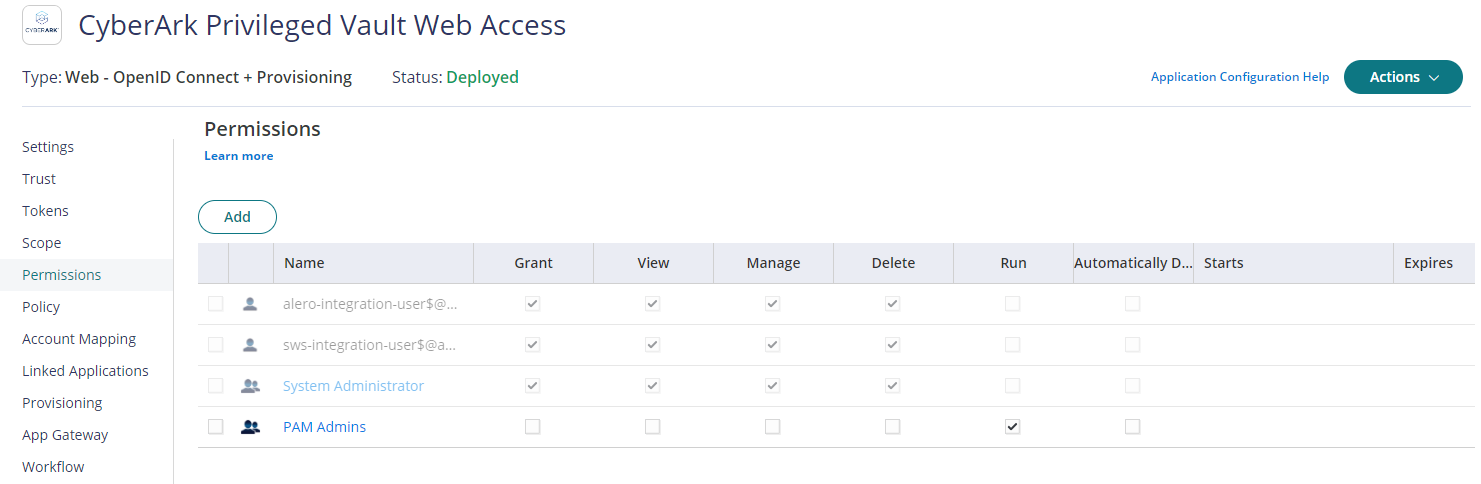
Click on Permissions tab, add above created role "PAM Admins" and select Run access then click Save to deploy.
Once Web App is saved, Identity Provider metadata can be requested using the URI https://<tenant_url>/<application_id>/.well-known/openid-configuration. This metadata will provide the information of endpoints, supported response types, default scopes & claims, etc.,
Optional: Customize the username claim returned in the id token to match with the username in CyberArk PVWA.
Click on Tokens tab, add below custom script to set custom claims on Script to set custom claims editor and click on Save. In this script, we are using LoginUser module to get and split username then set pvwa_username claim.
var username = LoginUser.Username;
var claim = username.split("@")[0];
setClaim("pvwa_username", claim);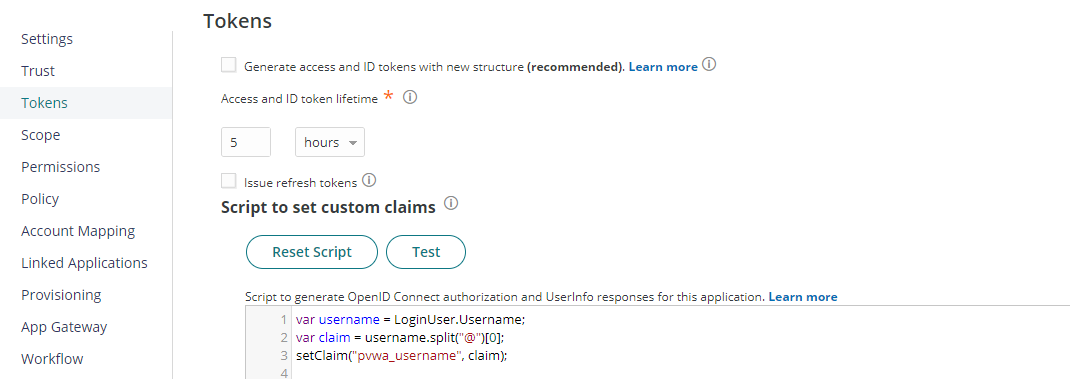
Make a note of following information from CyberArk Identity before you proceed to CyberArk PVWA
- OpenID Connect metadata URL
- OpenID Connect client ID
- OpenID Connect client secret
Create OIDC Authentication Method in CyberArk PVWA
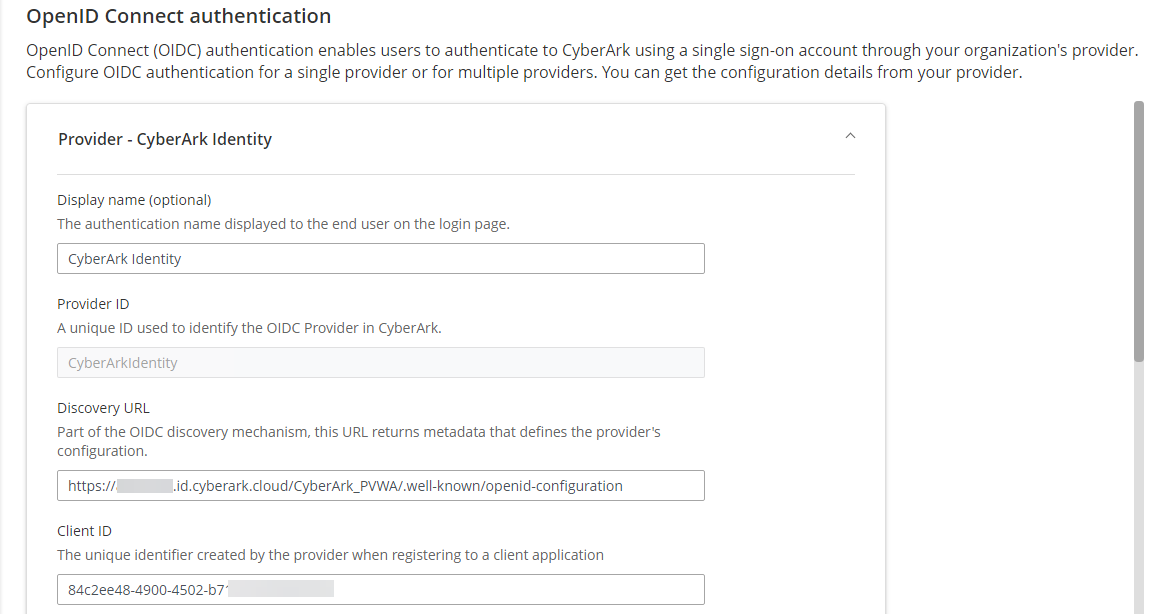
Log in to CyberArk PVWA and Navigate to Administration -> OIDC authentication. Enter the provider information as follows:
- Display name: Enter name to display to the end user on the login page
- Provider ID: Enter unique ID to identify the OIDC provider in CyberArk PVWA
- Discovery URL: Enter OpenID Connect metadata URL
- Client ID: Enter OpenID Connect client ID
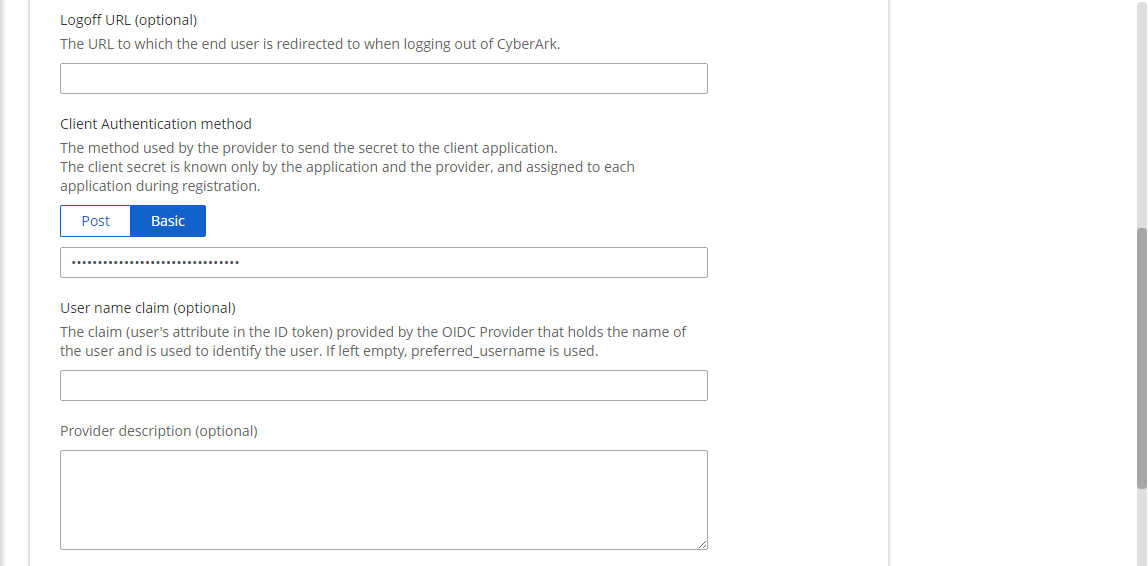
- Client Authentication method: Select Basic and enter OpenID Connect client secret
- User name claim: Enter Claim name provided by the OIDC provider to identify user. Default preferred_username.
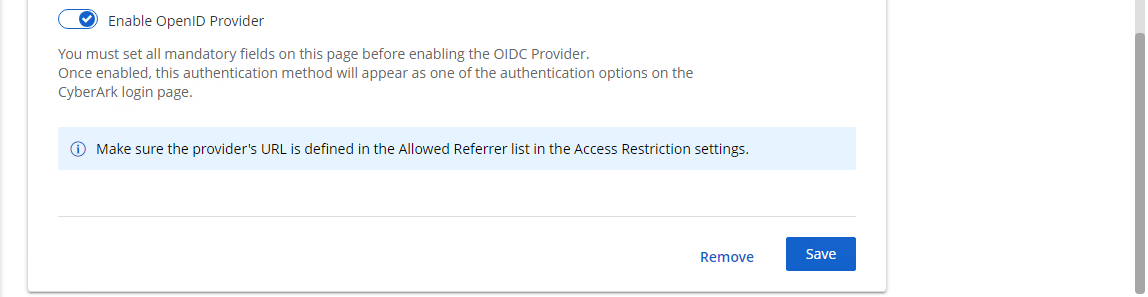
Enable OpenID Provider and click Save.
To define Provider's URL in the Allowed Referrer list in the Access Restriction Settings
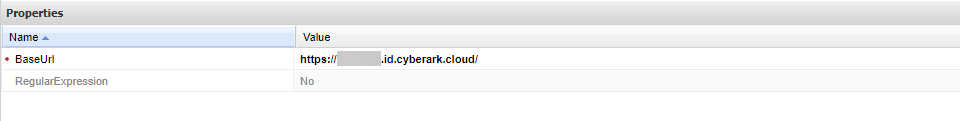
Navigate to Administration -> Configuration Options -> Options. Right click Access Restriction and select Add AllowedReferrer.
Enter CyberArk Identity's base URL in BaseUrl field.
Once OpenID provider is enabled, it will be available in the logon page for user to authenticate to CyberArk PVWA.
User successfully authenticated with OIDC provider but doesn't have an account in CyberArk PAS. User will be presented with authentication failure error.